ASYNCRAT-Command & Control Overview- 191.93.114.27
ASYNCRAT is a command and control (C&C) infrastructure that various cybercrime groups have used for a range of malicious activities. Its modular design allows it to be easily adapted for different types of attacks, making it a popular choice among threat actors.
191.93.114.27
This IP address is one of the servers ASYNCRAT uses for C&C communication. This server may be used to control botnets or other malicious activities.
| Month | Date Updated | CNC Attribution | IP Address | ASN | City | Geographic Country Location | Cloud Instance |
|---|---|---|---|---|---|---|---|
| Sep-2024 | 23 September 2024 | ASYNCRAT-Command & Control | 191.93.114.27 | 27831 | Barranquilla | Colombia | Colombia Movil, CO |
Technical Analysis of AsyncRAT
Infection Pattern – Phishing Page
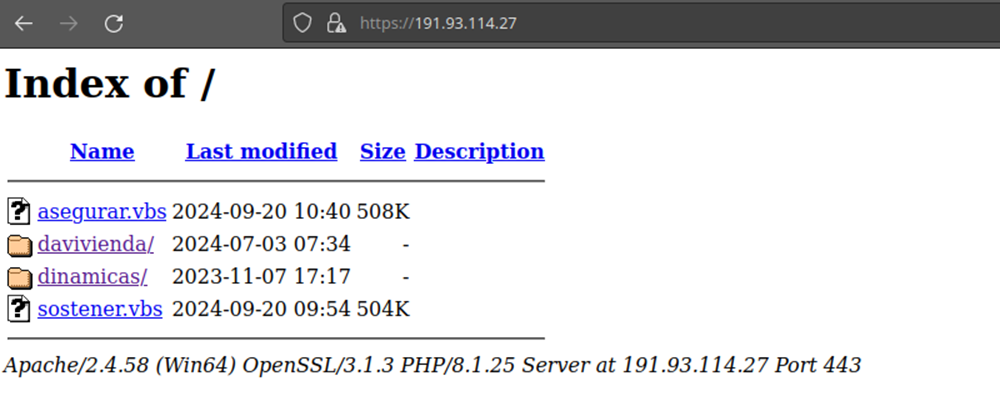
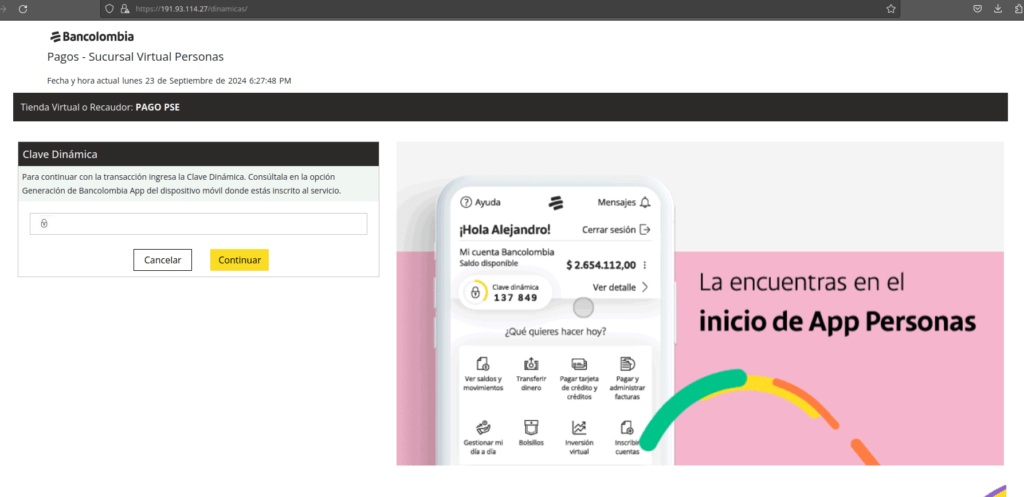
h[][][]://191.93.114.27/dinamicas/
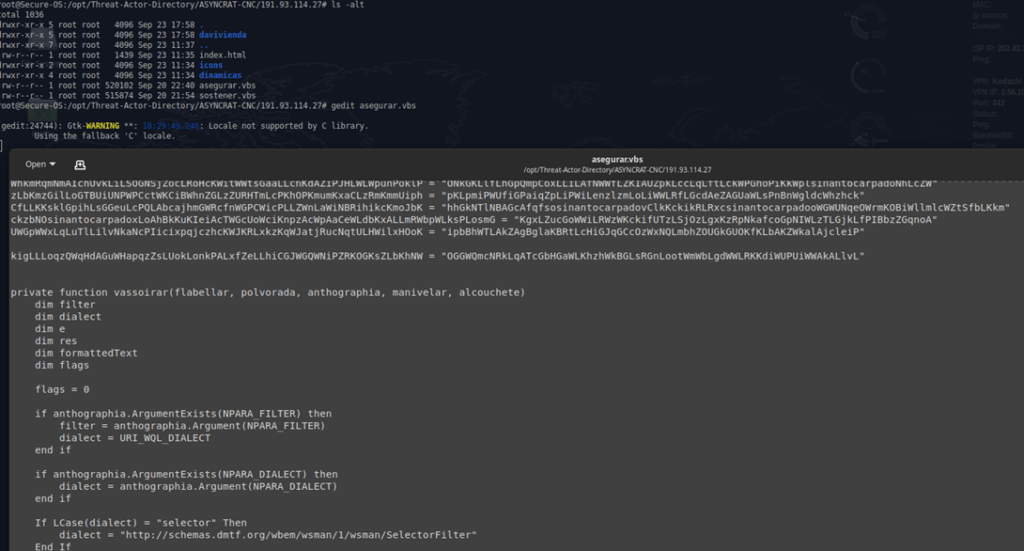
Malicious .vbs file – 191.93.114.27/asegurar.vbs
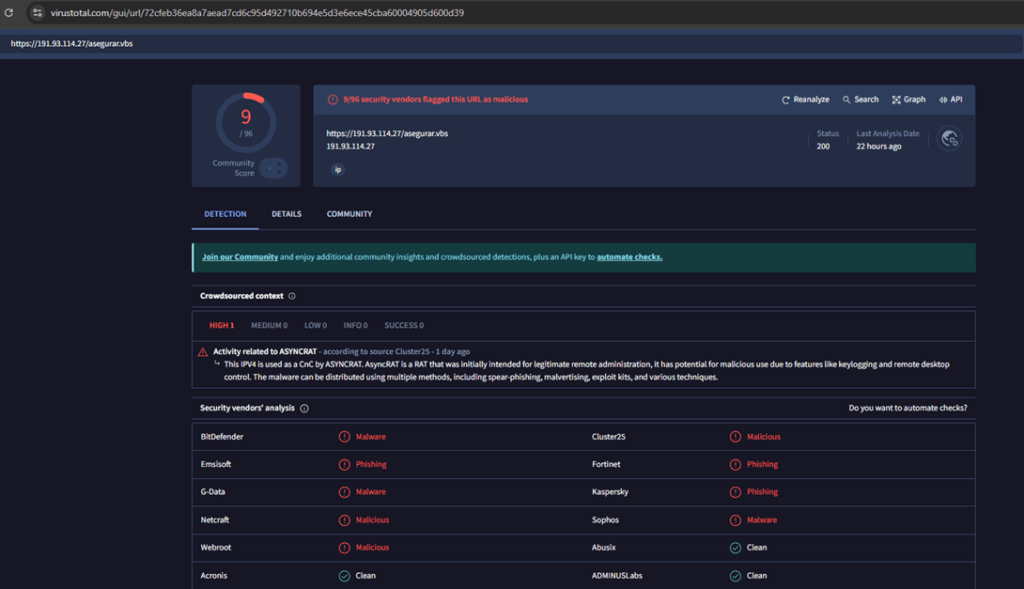
https://www.virustotal.com/gui/url/72cfeb36ea8a7aead7cd6c95d492710b694e5d3e6ece45cba60004905d600d39
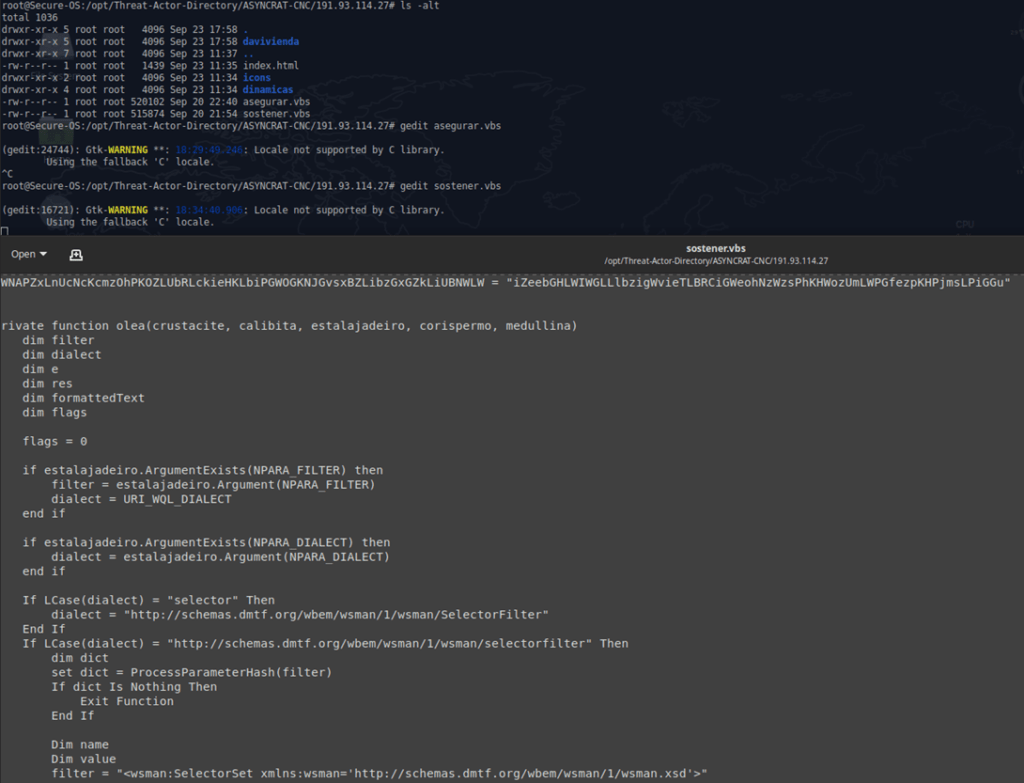
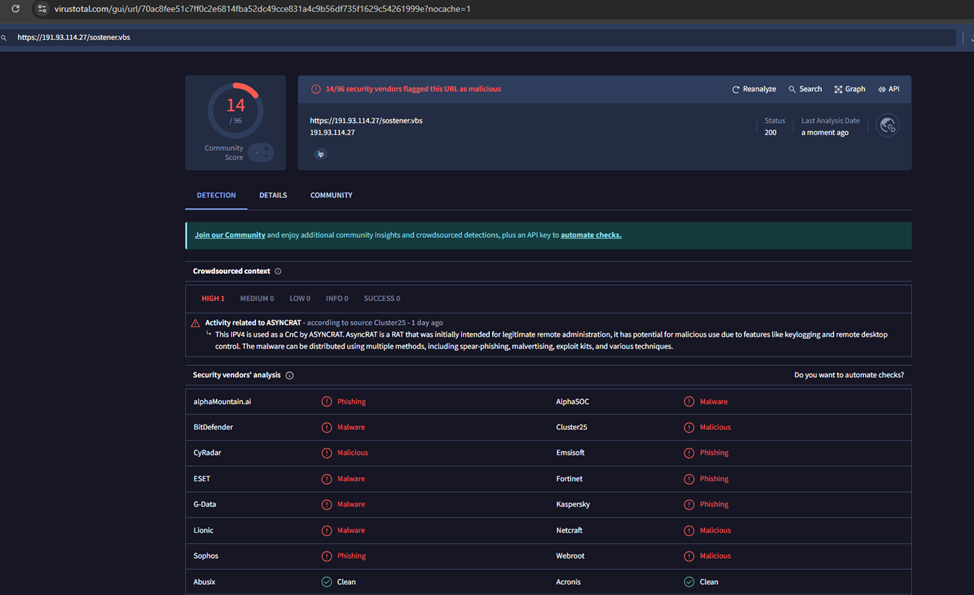
Malicious .vbs file – 191.93.114.27/sostener.vbs
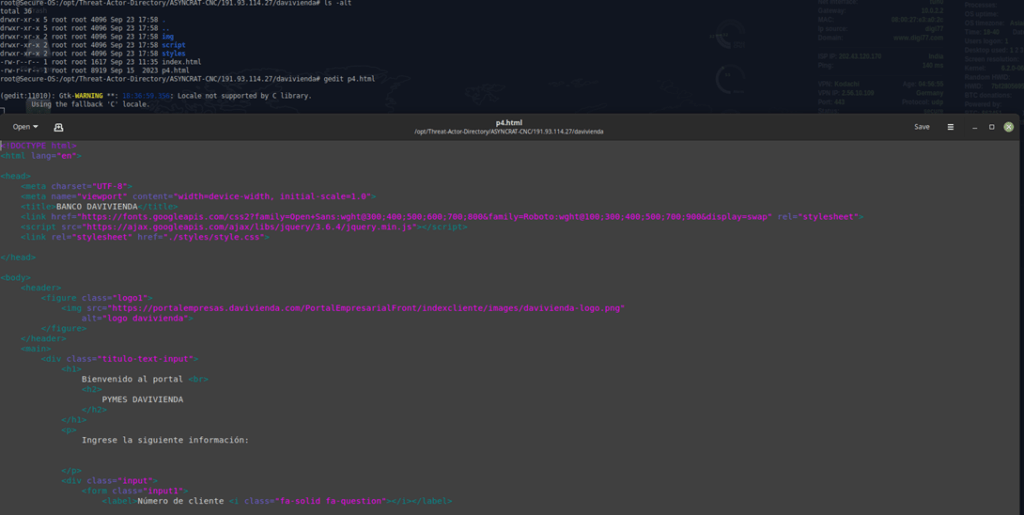
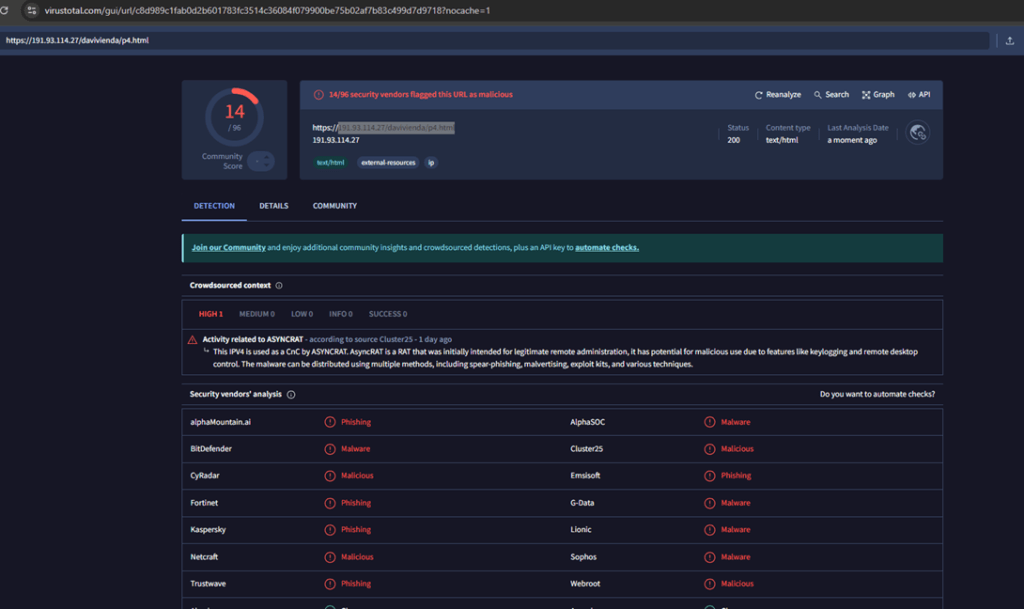
Malicious html file – 191.93.114.27/davivienda/p4.html
Understanding the Code
The provided HTML code appears to be a well-crafted phishing page designed to mimic the login page of a legitimate banking institution (Banco Davivienda). While the HTML itself is benign, the malicious intent lies in the JavaScript code (likely contained in script.js) that it loads.
How it works:
- Phishing: The page lures users into entering their sensitive information (username, password, etc.) by impersonating a trusted financial institution.
- Data Exfiltration: Once the user submits the form, the JavaScript code captures the input data and sends it to a malicious server controlled by the attacker.
- Additional Actions:
- Keylogging: The JavaScript might include keylogging functionality to capture additional keystrokes, including passwords for other websites.
- Drive-by Downloads: The script could download and execute additional malware onto the victim’s machine.
- Remote Access: It might establish a remote connection to the victim’s computer, allowing the attacker to control it.
- Keylogging: The JavaScript might include keylogging functionality to capture additional keystrokes, including passwords for other websites.
YARA Rules for Detection
Creating YARA rules to detect this kind of attack can be challenging due to the dynamic nature of malicious JavaScript. However, we can focus on some common indicators:
1. Base64-encoded JavaScript:
rule malicious_base64_js
{
strings:
$a1 = “base64,”
$a2 = “<script>”
condition:
$a1 and $a2
}
2. Unusual HTTP requests:
rule suspicious_http_request
{
strings:
$a1 = “http://[.]baddomain[.]com/” nocase
$a2 = “POST”
condition:
$a1 and $a2
}
3. Command and Control (C2) communication:
rule c2_communication
{
strings:
$a1 = “eval(“
$a2 = “function”
condition:
$a1 and $a2
}
4. Obfuscated JavaScript:
rule obfuscated_js
{
strings:
$a1 = “[a-z]{2,}\((.*)\)”
$a2 = “eval”
condition:
$a1 and $a2
}



