The Rise of AI-Enhanced Malware Developers: A Deep Dive into CaaS, Credential Theft & Exploit Distribution
1. Key Takeaways
Overview of rising cybercrime activity
-
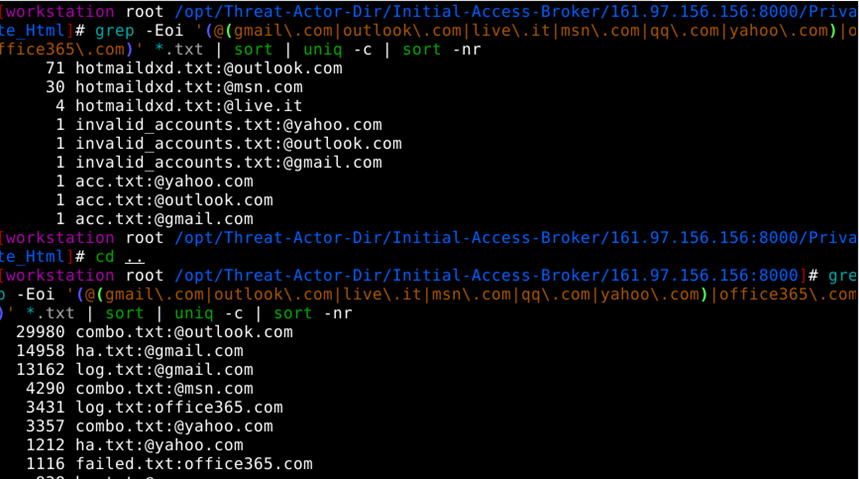
We at Threatactix Research team identified a campaign that started from 9th September 2025, in which an attacker attempted multiple SMTP-related exploits to compromise/access approximately 1,30,164 credentials from office365.com, gmail.com, qq.com, outlook.com, hotmail.com, and others.
-
Investigation has linked this actor to the XWorm cybercrime ecosystem, an entity primarily engaged in credential compromise activities. The actor’s motivation, coupled with their confirmed access to sensitive credentials, indicates a high likelihood of a mass distribution campaign for XWorm. This distribution model allows threat actors to leverage the compromised credentials for effective social engineering, crafting highly convincing spear-phishing emails that deliver infected attachments. This chain of events frequently results in malicious file downloads and the proliferation of exploit kits targeting unpatched software vulnerabilities (e.g., in web browsers or third-party plugins).
- Why were these tools so effective? this IAB used 5 AI toolsets to enhance vulnerability and scanning activities. By embedding these tools in the workflow, the attacker used Machine Learning and AI capabilities to improve the tools’ performance. Also, we have discovered AI like Grok used first time for a new tool named ‘Pulsar’.
-
- Grok – used in the new tool name Pulsar
- Anthropic – Claude used in the OneForAll tool-[ Earlier in Anthropic also shared threat intelligence, but we believe this could be another threat actor ]
- Z.ai – used in a new scanner named Red-ultra-scanner-project
- Blackbox.ai
- Huggingface.ai
-
4. We discovered new toolsets that are related to AI and ML enhancement in their vulnerability scanning and exploitation patterns.
1. Red-Ultra or Red-Enhanced-Scanner
2. Nexus–inspired by combining DOFFS BOT with Nexus-inspired scanning techniques
3. Pulsar-V2 – This tool is enhanced with Grok AI capabilities
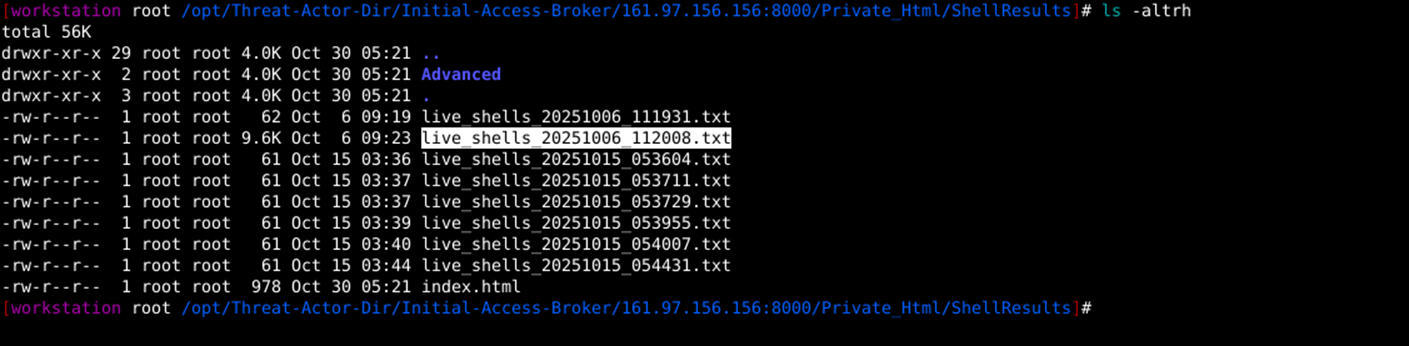
5. Also, on further validation, the Threat Actor had unauthorized access on 4 amazonaws.com instances, in which 66 webshells were installed. We also discovered settings related to office365.com and zoho.com, which suggested that future attacks will involve the zoho.com attack surface. We could not discover credentials related to zoho.com at the time of analysis of the C2 server.
2 Indicators Discovered on the Server – Attack Timeline
2.1 Usage of the 5 AI toolset in Offensive toolset enhancements
1. The threat actor used at least 5 AI tools to engage AI and Machine Learning capabilities like Grok, Anthropic-Claude, z.ai, Huggingface, and Blackbox.ai.
1. Grok and Anthropic were used for the enhancement of the “Pulsar” tool
2. Z.ai is used for the enhancement of “red-ultra-scanner-project.”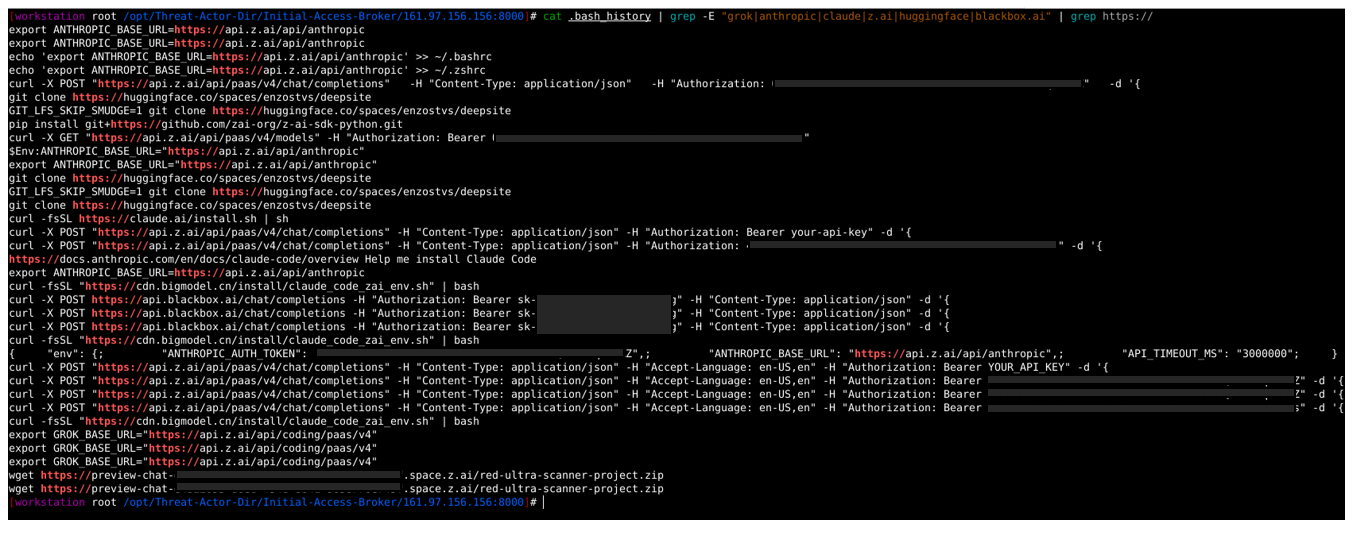 2. On further validation, we discovered settings.json files available on the C2 server, suggesting Grok and Claude were used for further enhancement of the Pulsar tool. These files transform generic tools into tailored, efficient agents by automating overrides, integrations, and preferences without manual flags each time. These configuration files directly enable and enhance the project’s development workflow by integrating powerful AI models. In essence, they enhance the developer’s productivity and the quality of the code by intelligently integrating AI assistance.
2. On further validation, we discovered settings.json files available on the C2 server, suggesting Grok and Claude were used for further enhancement of the Pulsar tool. These files transform generic tools into tailored, efficient agents by automating overrides, integrations, and preferences without manual flags each time. These configuration files directly enable and enhance the project’s development workflow by integrating powerful AI models. In essence, they enhance the developer’s productivity and the quality of the code by intelligently integrating AI assistance.
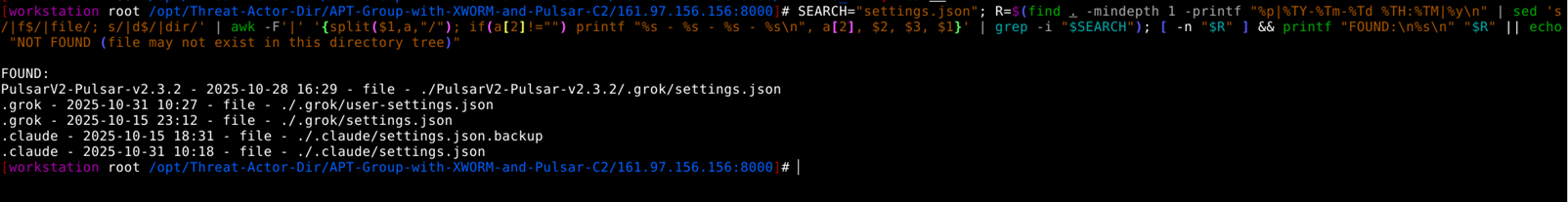
3. The usage of the specified files inside tool directories is as follows:
- ./.grok/settings.json: This file is used by the Grok CLI tool for configuration settings specific to a project or environment. At the project level,
- ./.grok/settings.json (project-level) overrides global defaults for models and MCP servers (e.g., Linear integration for issue management), allowing project-specific AI behaviors like faster code editing with Morph Fast Apply at 4,500+ tokens/sec../.grok/user-settings.json: At new project enhancement level.
- ./.grok/user-settings.json (user-level, often in home dir but project-aware) sets API keys, base URLs, and default models globally, streamlining authentication, model selection, and fallback logic across projects for seamless terminal AI workflows.
- ./.claude/settings.json.backup: This file is a backup of the ./.claude/settings.json file, but according to some sources, files like .claude.json and its backups are deprecated and no longer supported in newer versions of Claude Code tools../.claude/settings.json: It controls Claude Code’s behavior within a project.
- /.claude/settings.json configures tool permissions, observability, and shared project settings, directly controlling AI behavior and integrations within the project
2.2 Distribution of Stealers, SMTP Exploits, Webshells, and Account Crackers
- From .bash_history analysis, we discovered that the Threat Actor used approximately 66 Python scripts for various tasks focused on accomplishing tasks like AI-driven vulnerability as well as credential scanning, SMTP getaways, and credential cracking activities. These scripts enhanced efficiency by merging AI insights with pen testing workflows, enabling scalable attacks on web apps and networks
- The threat actor uses mostly SMTP stealers and email cracking techniques to get access to various platforms’ credentials. As an output of these scripts, Threat Actor was able to compromise credentials from various Email providers like office365.com, gmail.com, qq.com, outlook.com, Hotmail.com, etc. Overall, we discovered approximately 1,30,164 credentials stored in various files.
- This actor is one of the members of the XWorm Stealer ecosystem and consists of XWorm-5.6-source code for further operations.
- Along with compromised credentials, this actor was able to plant/upload various webshells on Amazon AWS instances. We have identified 4 unique instances where 60+ webshells are installed.
- From the command-and-control server, we discovered there are 3 new tools listed, which are currently new to the global attack surface.
1. Red-ultra-scanner
2. PulsarV2
3. Nexus
2.3 Threat Actor activity timeline
Campaign Activity in September 2025 – Threat Actor / Malware developer used multiple Python scripts. As per campaign tracking and .bash_history analysis revealed activity started on 9th September 2025, where the ah.py script was executed. This script is related to the Multi-Protocol AI-driven vulnerability and Credential scanner.
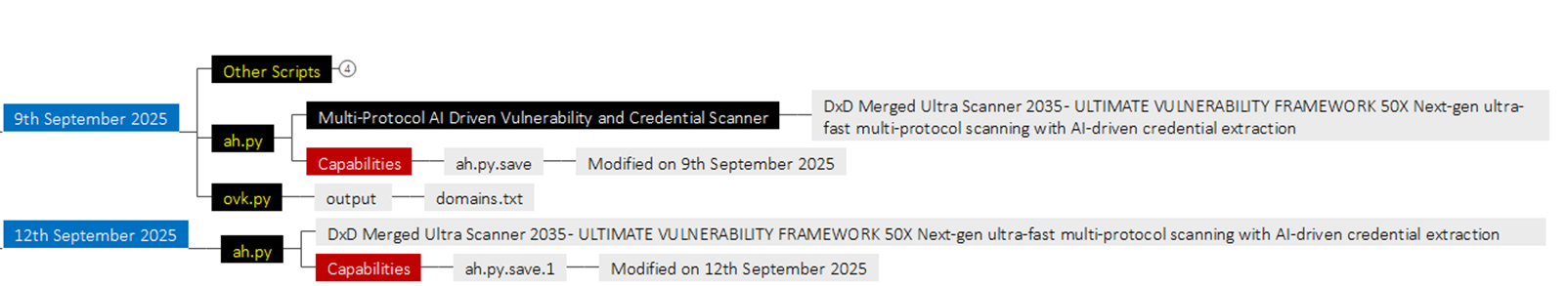
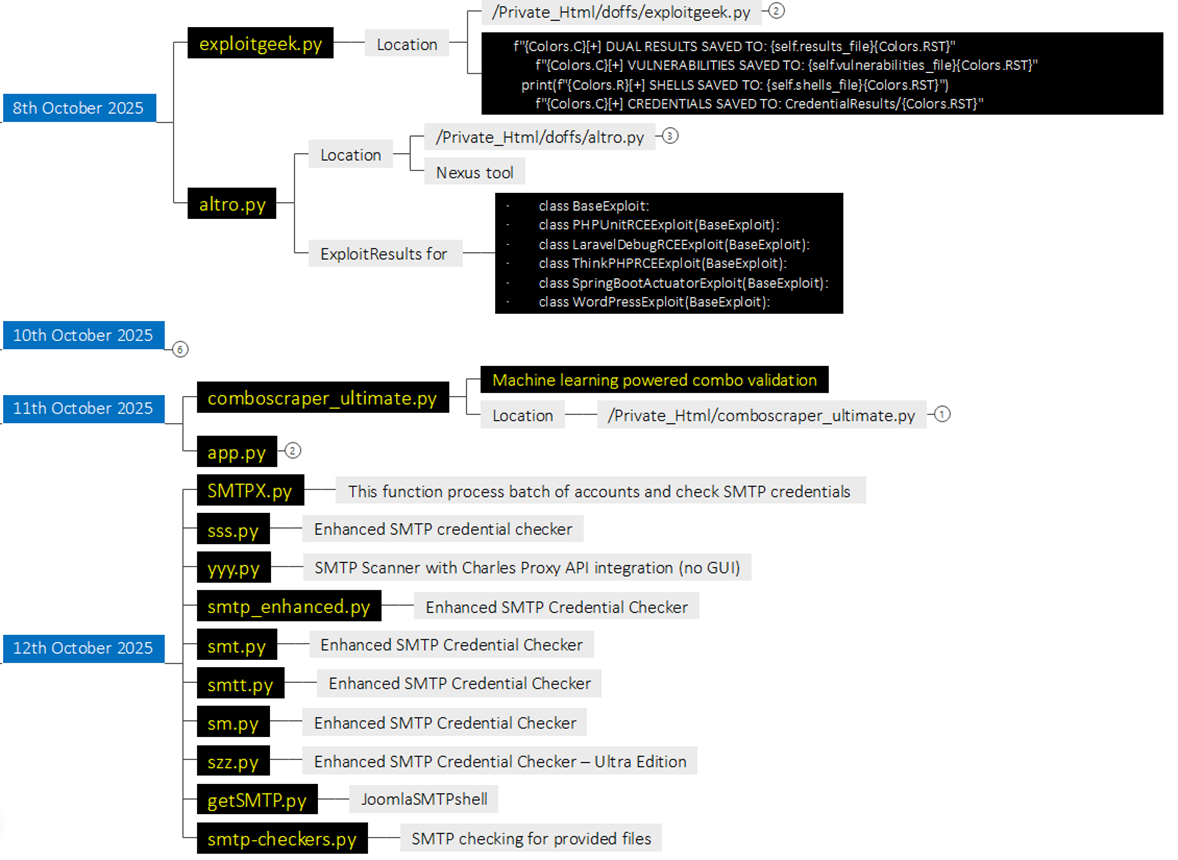
Campaign Activity in October 2025 -Next iteration, the attacker attempted various script activities on 8th October 2025, in which the Threat Actor executed exploitgeek.py and altro.py.
- Exploitgeek.py is a Next-gen ultra-fast multi-protocol scanning with AI-driven credential extraction, adaptive scanning strategies, and real-time analytics dashboard integration. This script has the Functionality of extracting credentials from AWS, SMTP, Database, and API Keys.
- Altro.py is a variation of Nexus Tool – A comprehensive security toolkit combining DOFFS BOT with NEXUS-inspired scanning techniques.
- comboscraper_ultimate.py is a Machine learning powered combo validation script capable of Machine learning combo validation, a RESTful API for remote management, and Telegram/Discord notifications.
- We observed from 12th October 2025 till 25th October 2025, various SMTP-related scripts executed, which are capable of processing a batch of accounts and checking SMTP credentials, SMTP Scanner with Charles Proxy API integration (no GUI).
2.4 Presence of XWorm Malware Source Code
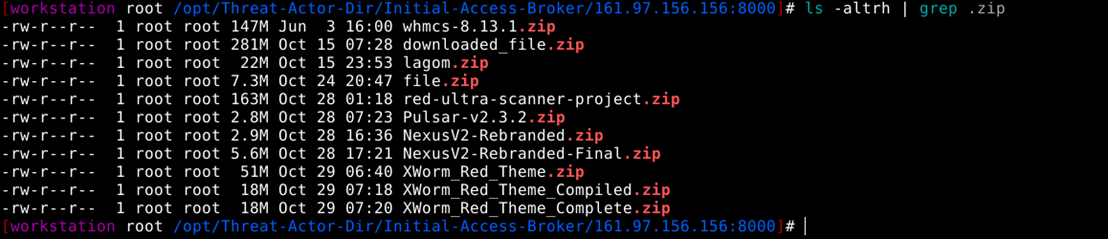
1. XWorm activity from November 2025 – Post credential access, the attacker had downloaded multiple XWorm source code files. As from the C2 server access, these files were available to download from 29th October 2025 till 7th November 2025, indicating the attacker’s motivation to escalate credential access to malware delivery attempts
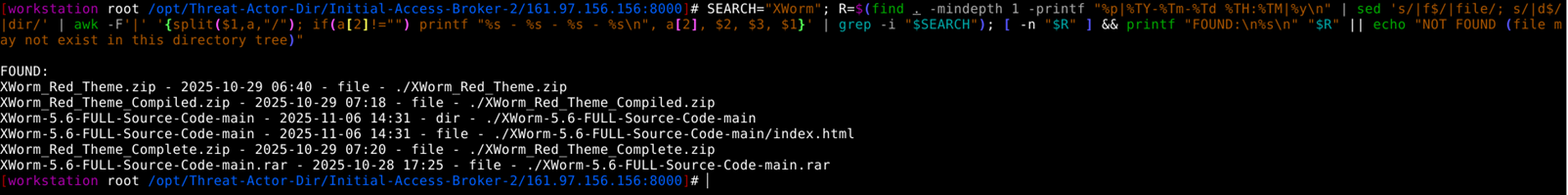
2. Directory Listing of XWorm captured on 6th November 2025.
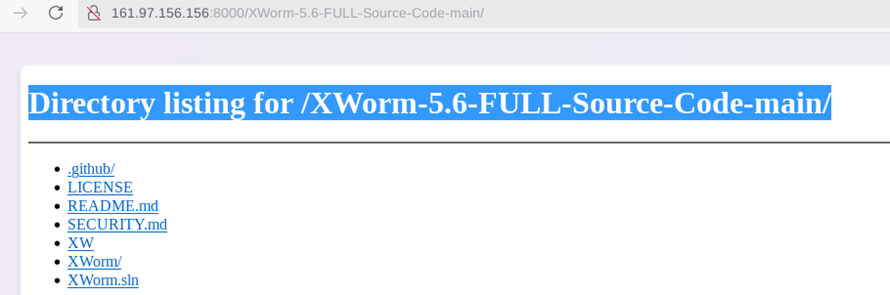
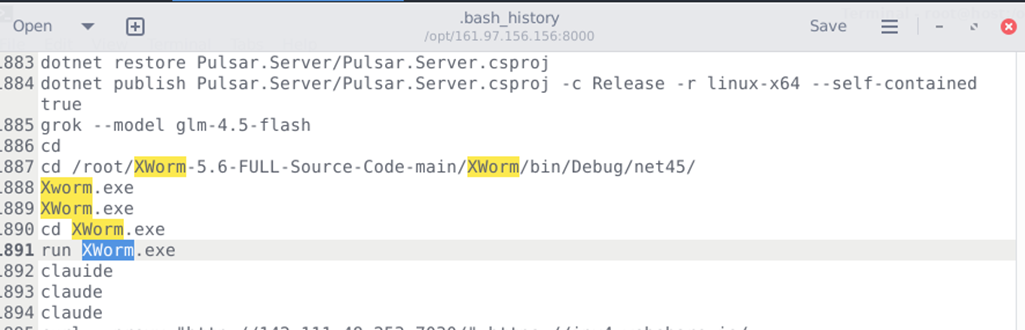
3. As per the .bash_history analysis, the attacker attempted to execute XWorm.exe multiple times.
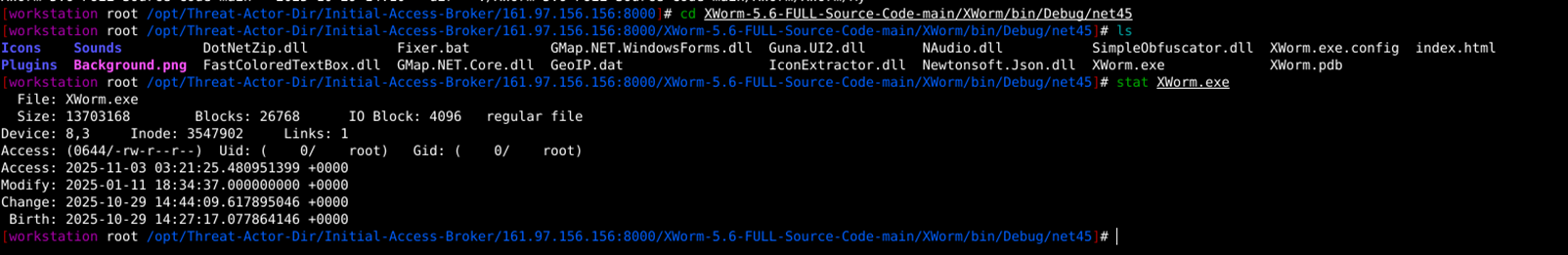
4. As per timeline analysis, via stat identified that XWorm.exe was last modified on 11th January 2025, as its version 5.6 suggested. This file was downloaded on the C2 server on 29th October 2025.
2.5 Stolen Credentials activity
We found multiple credential-related files in the folder /Private_Html/doffs location. As per the internal scripts description, this toolset is advertised as “DOFFS NEXUS EDITION – Ultimate Cybersecurity ToolKit”. The DOFFS NEXUS Edition is presented as an “Ultimate Cybersecurity Toolkit” that combines:
- DOFFS BOT: This component probably refers to an automated bot or script (BOT) used for certain defensive or offensive cybersecurity tasks. While “DOFFS” is not a universally recognized acronym in this context, the association with a “BOT” suggests an automated tool, possibly for tasks like scanning, data collection, or exploit execution. The term “bot” in cybersecurity is often associated with malicious botnets (a network of compromised computers)
- Nexus Inspired Scanning Techniques: This indicates the toolkit incorporates methodologies or features similar to those found in established cybersecurity platforms or concepts named Nexus. Sophisticated scanning and analysis capabilities (the Nexus Inspired Scanning Techniques) focused on vulnerability detection, cyber risk assessment, or software component analysis.
- The overall goal of such a toolkit would be to provide a powerful, integrated solution for proactively identifying and managing security vulnerabilities and risks in systems and applications.
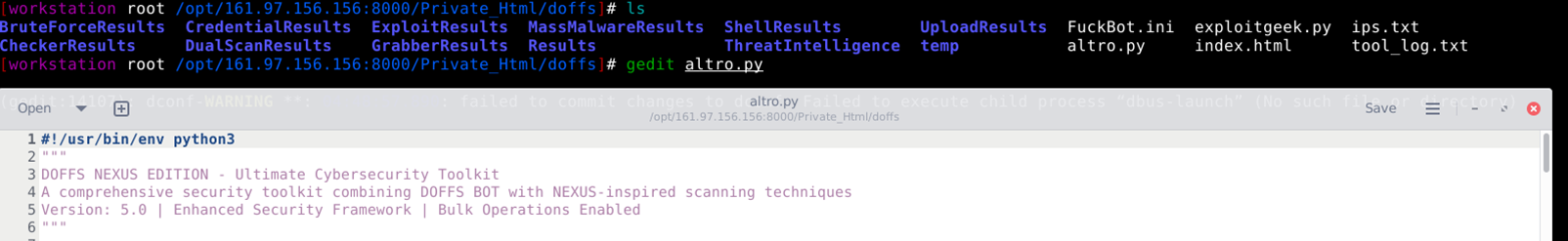
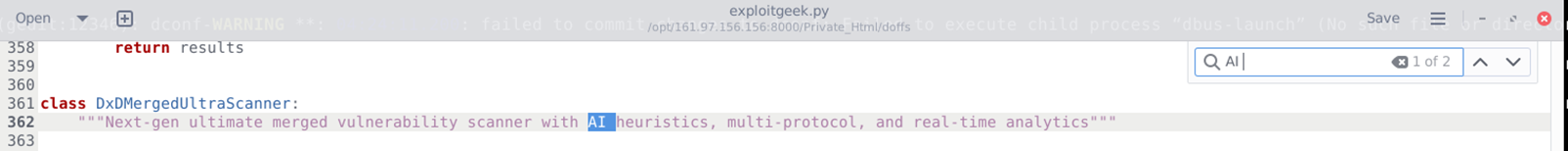
What is not verified or seems suspicious about “DOFFS NEXUS Edition”
- There are no credible sources (articles, GitHub repos, vendor pages, security‑community entries) for anything called “DOFFS NEXUS Edition”. A large web search came up empty.
- There is no evidence for a tool called “DOFFS BOT” in public cybersecurity tooling, as no mention in open‑source directories, cybersecurity vendor lists, or threat‑tool databases.
- Because neither “DOFFS NEXUS Edition” nor “DOFFS BOT” appears to exist publicly, this name could likely be:
1. A proprietary/internal tool (not publicly disclosed)
2. marketing‑coined phrase (maybe in a job posting, private offering, or non‑professional context)
3. A misunderstanding / mis‑naming — perhaps mixing names of other tools (e.g., “Nexus scanner”) with something else, leading to a hybrid but incorrect label.
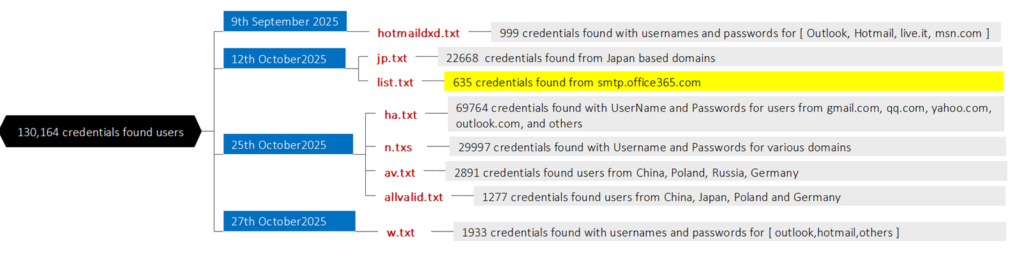
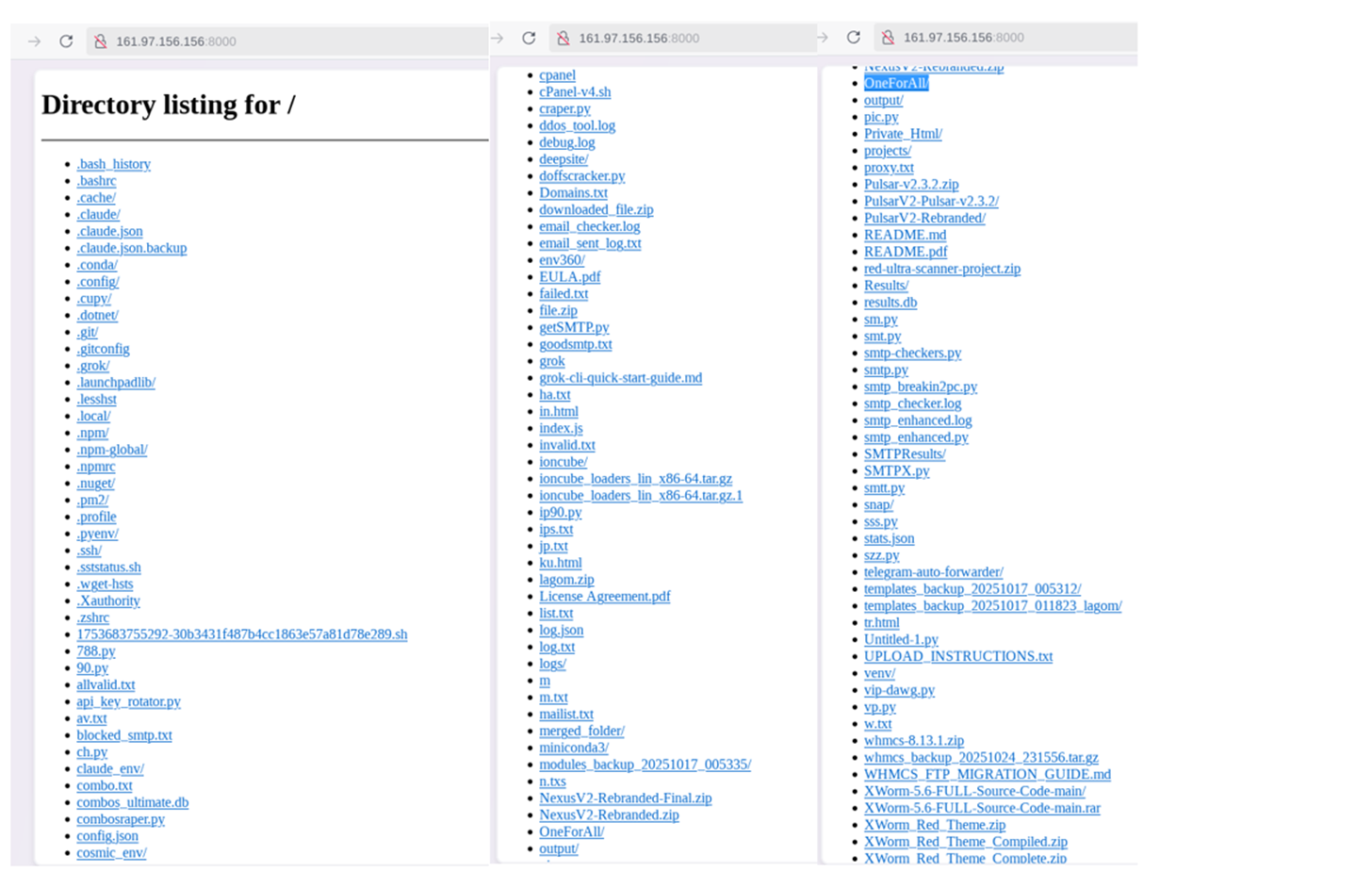
Directory listing found on 6th November 2025.
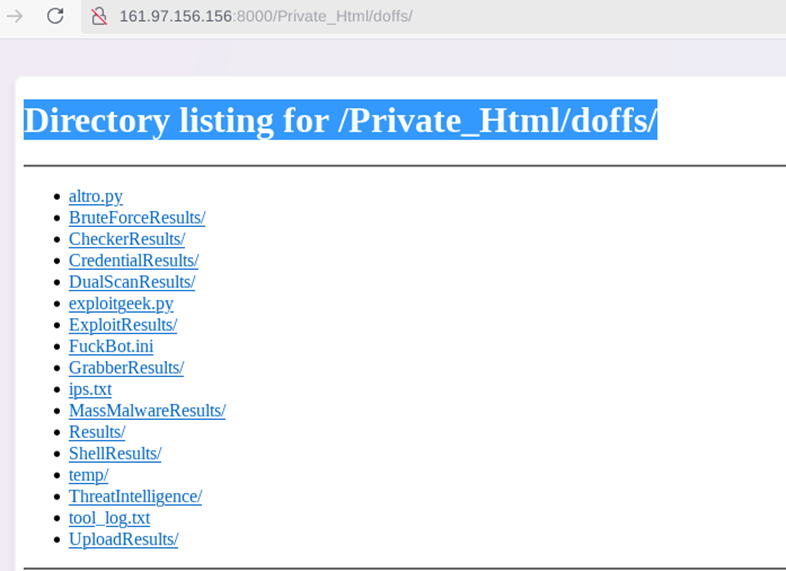
This screenshot depicts multiple files available as below folders
- Output files from the folder /Private_Html/doffs — this folder contains multiple files updated on 15th October 2025, which is likely the timestamp when these tools were executed.
- Multiple Python files were executed between 12th October 2025 and 25th October 2025. A deeper analysis reveals that these files ran with multiple fine-tuning adjustments and iterations during this period.
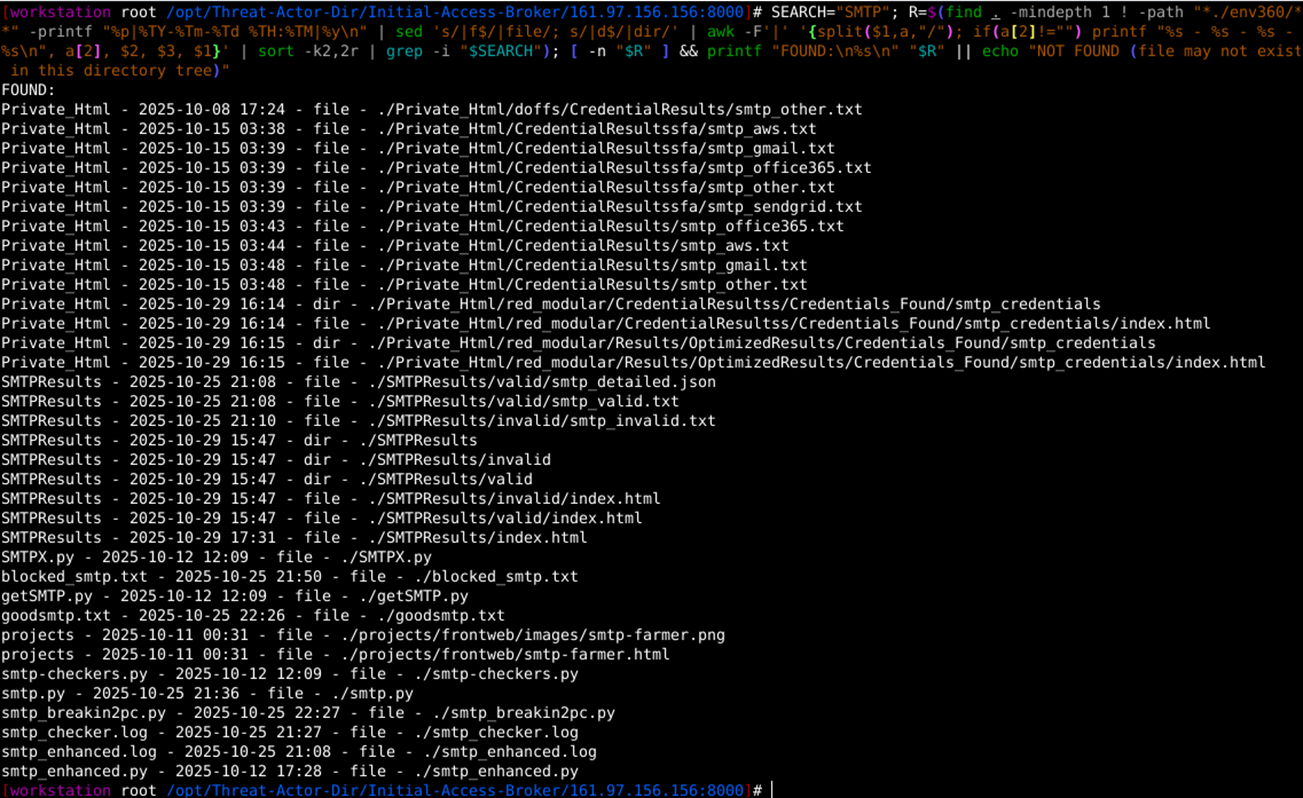
3. Impact on victims – On detailed analysis, we identified multiple .txt files in which credentials were stored might result of the credentials-related Python files execution. On further validation, we discovered that around 130,164 credentials were stored from Gmail.com, Outlook.com, office365.com, and live.it, msn.com, qq.com, yahoo.com, and others.
2.6 Amazon AWS Servers with Live Webshell
Web shells are malicious scripts uploaded to web servers to enable remote command execution and control. They are commonly used by attackers to gain persistent access, maintain control, and facilitate lateral movement within a compromised network. Specifically, web shells allow threat actors to execute commands, upload/download files, escalate privileges, gather information, and move laterally to other systems, helping them persist and expand their access within the environment.
Therefore, uploading web shells on 4 Amazon AWS instances on 6th October 2025 likely indicates an attempt to establish persistence and carry out lateral movement in the network. These web shells serve as covert access points for attackers to maintain their foothold and expand control over other network resources from the compromised servers.
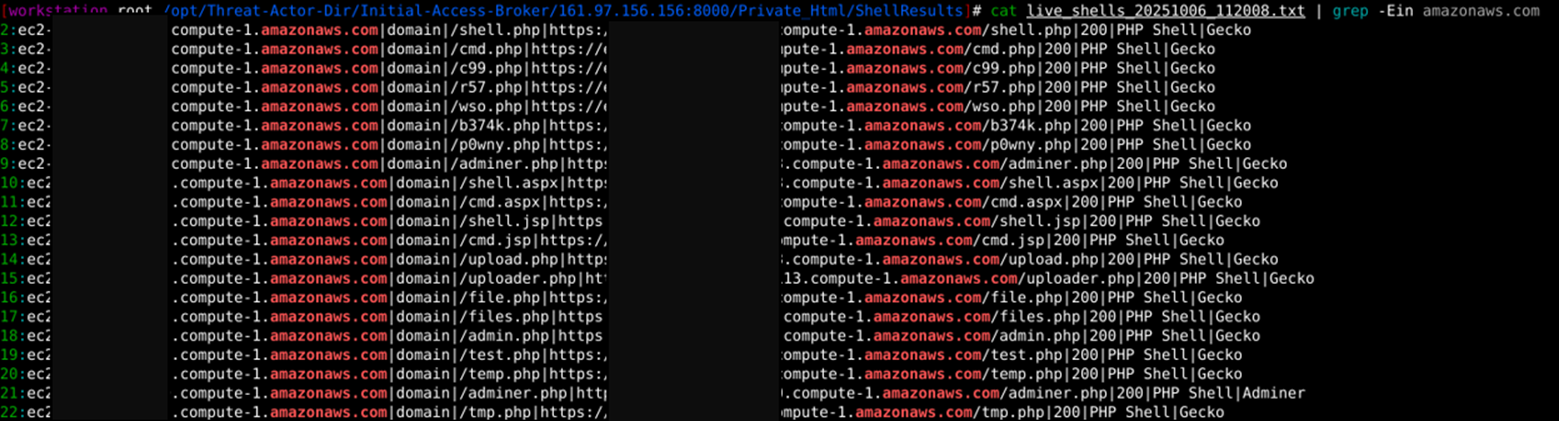
We have identified multiple types of webshells attempted to upload to Amazon AWS instances.
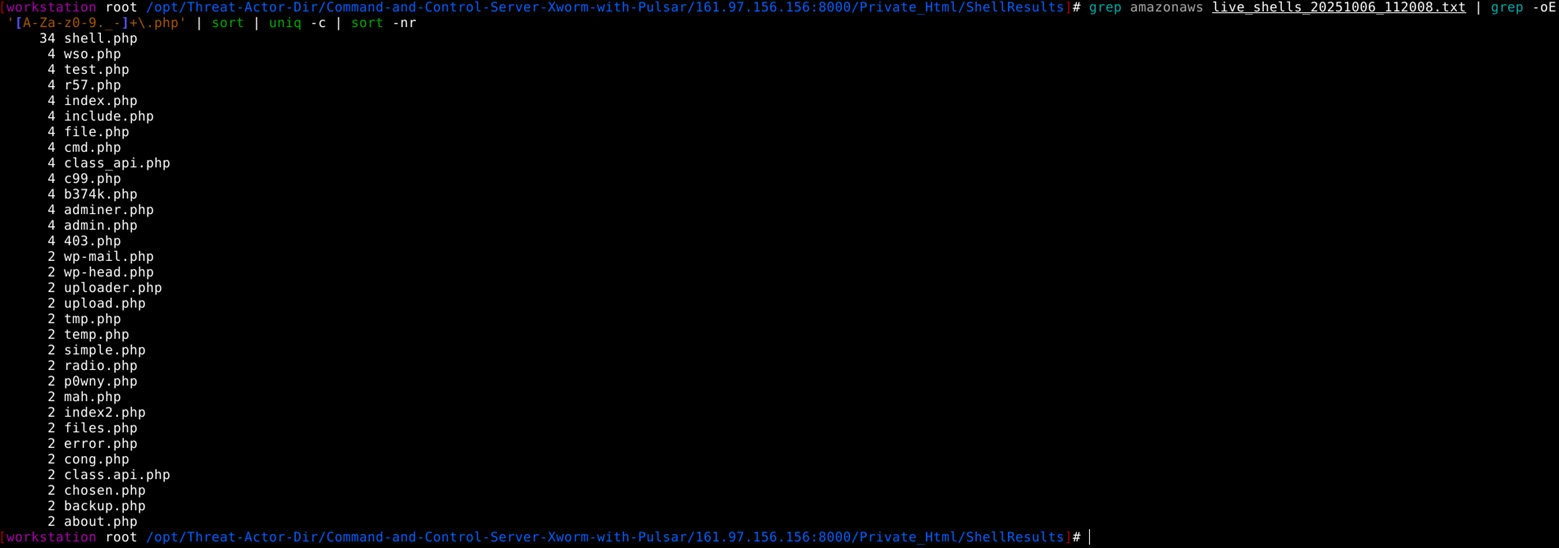
3 Behavioral Profile of the Threat Actor
Criminal Ecosystem Alignment – Resembles dark-web exploit sellers
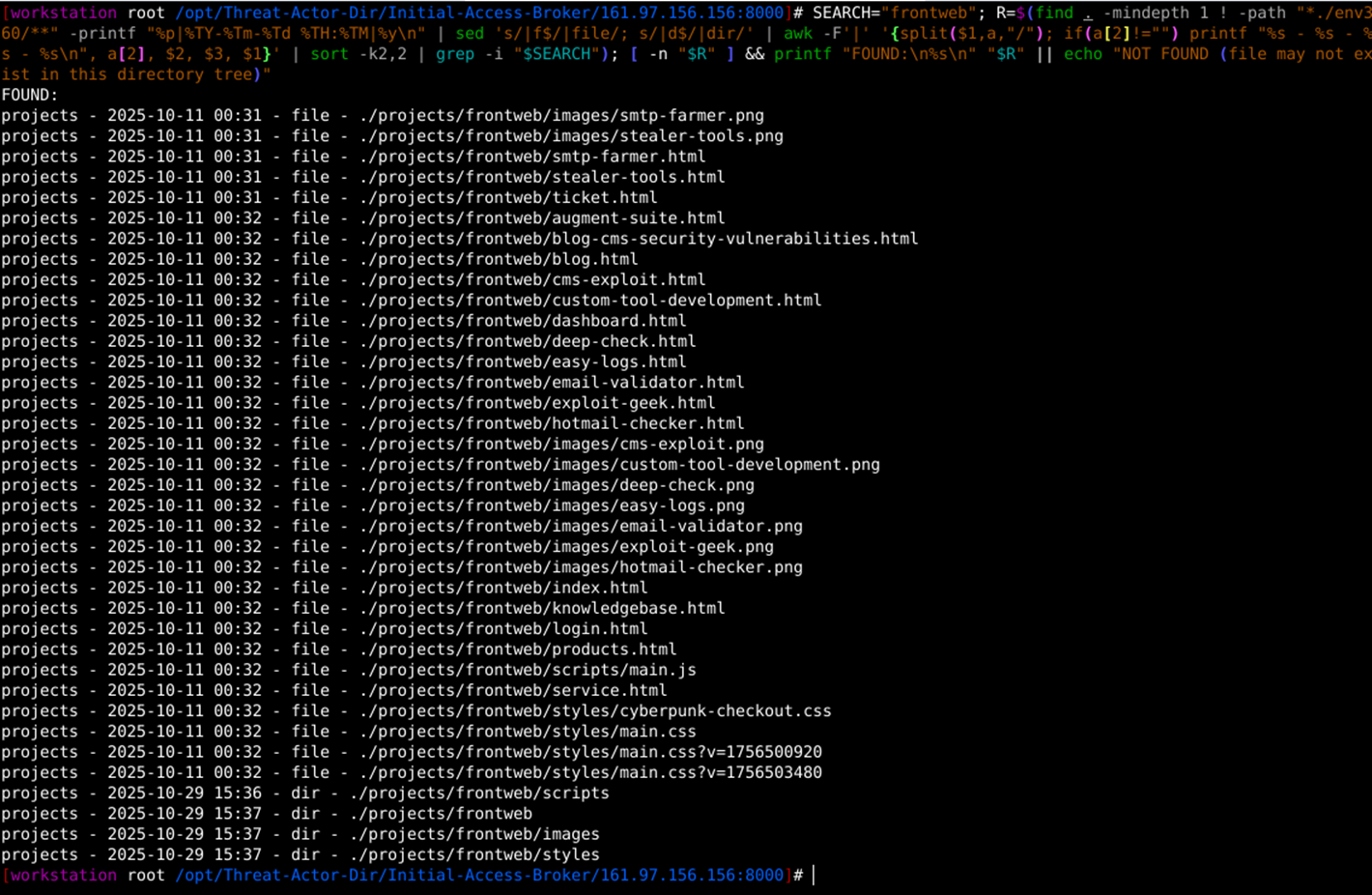
1. Also, on a further deep dive, we have discovered multiple toolsets that can be used for offensive activities and listed on 11th October 2025. The listed files—such as blog-cms-security-vulnerabilities.html, cms-exploit.png, and others like deep-check.png, easy-logs.png, and stealer-tools.png.png—appear to document tools potentially usable for offensive cybersecurity operations, including CMS exploits, log analysis, email validation, and malware stealers. These align with common offensive security toolkits for tasks like vulnerability scanning, brute-forcing, and credential extraction, often found in cheat sheets or GitHub repositories. No exact matches for these specific filenames surfaced in public sources, suggesting they may stem from private threat intelligence or custom pentesting reports
- blog-cms-security-vulnerabilities.html
- cms-exploit.png
- custom-tool-development.png
- deep-check.png
- easy-logs.png
- email-validator.png
- exploitgeek.png
- hotmail-checker.png
- smtp-farmer.png
- stealer-tools.png
2. Potential Uses and Examples
-
- CMS and Exploit Tools (e.g., blog-cms-security-vulnerabilities.html, cms-exploit.png, exploit-geek.png): Target content management system weaknesses via exploits, akin to tools for SQLi, XSS, or directory bruteforcing.
- Validation and SMTP Tools (e.g., email-validator.png, hotmail-checker.png, smtp-farmer.png): Verify emails or farm SMTP servers for phishing or spam campaigns, similar to web attack enumeration techniques.
- Logging and Stealer Tools (e.g., easy-logs.png, stealer-tools.png): Simplify log extraction or deploy infostealers for credential theft, as seen in AI-assisted malware generation.
- Scanning and Custom Tools (e.g., deep-check.png, custom-tool-development.png): Perform deep vulnerability checks or build bespoke offensive scripts, mirroring manual analysis in pentesting
4. Threat Actor Infrastructure Discovery
During our OSINT analysis, on 29th October 2025 and revalidation on 6th November 2025, we have identified one of the Open DIR hosting multiple malicious tools and directories, which indicates this is one of the significant threat actors and is using these toolsets for large-scale compromise attempts.
- First Discovery – https://urlscan.io/result/019a3006-2beb-773c-9f97-5aba7241c038/
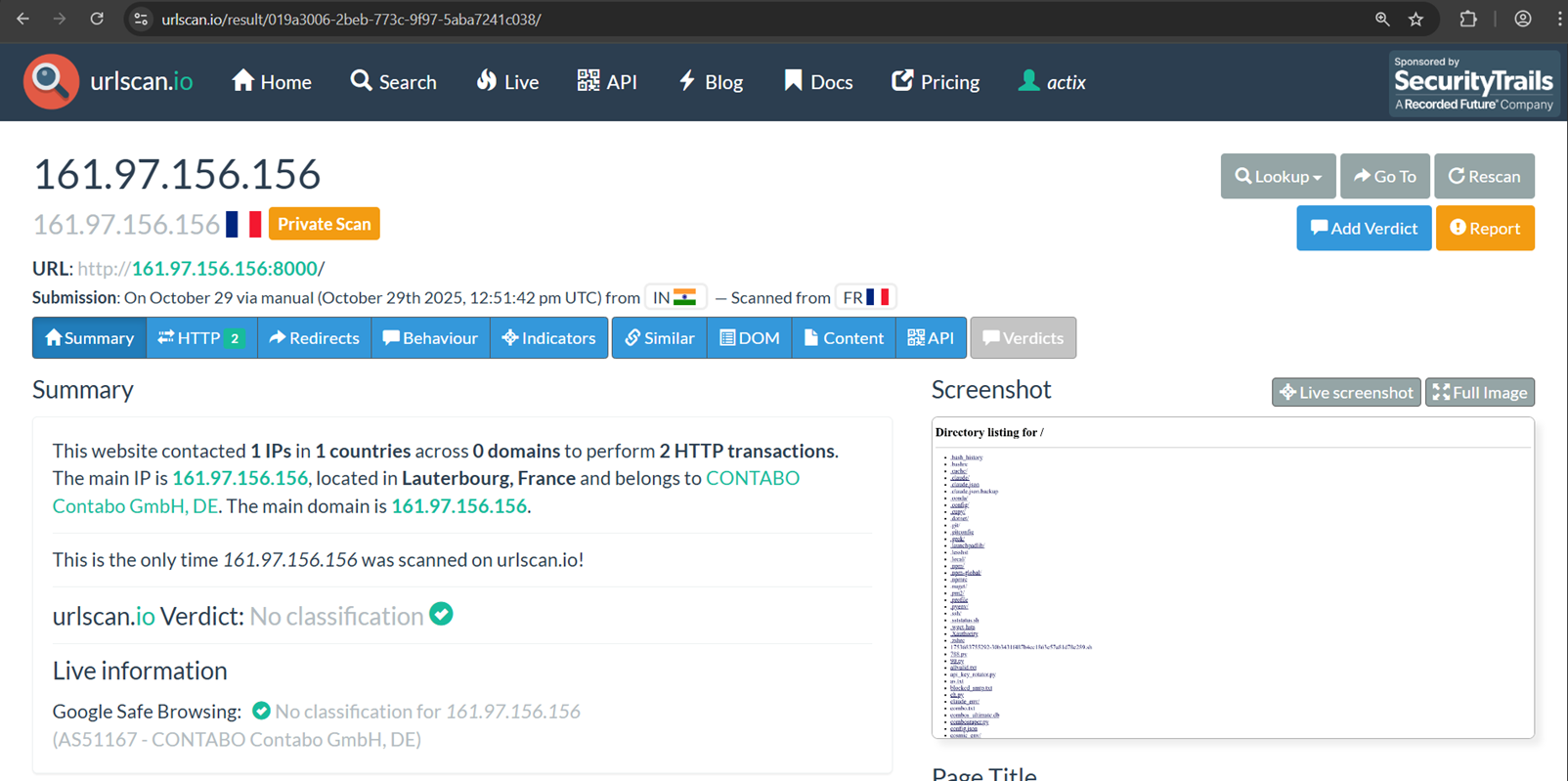
Online activity validation – As checked, the Threat Actor was live till 6th November 2025. Threat Actor C2 infrastructure was found down on 15th November 2025.
Second Discovery – https://urlscan.io/result/019a5b6f-559b-76fb-9cc6-f5d324078eb9/
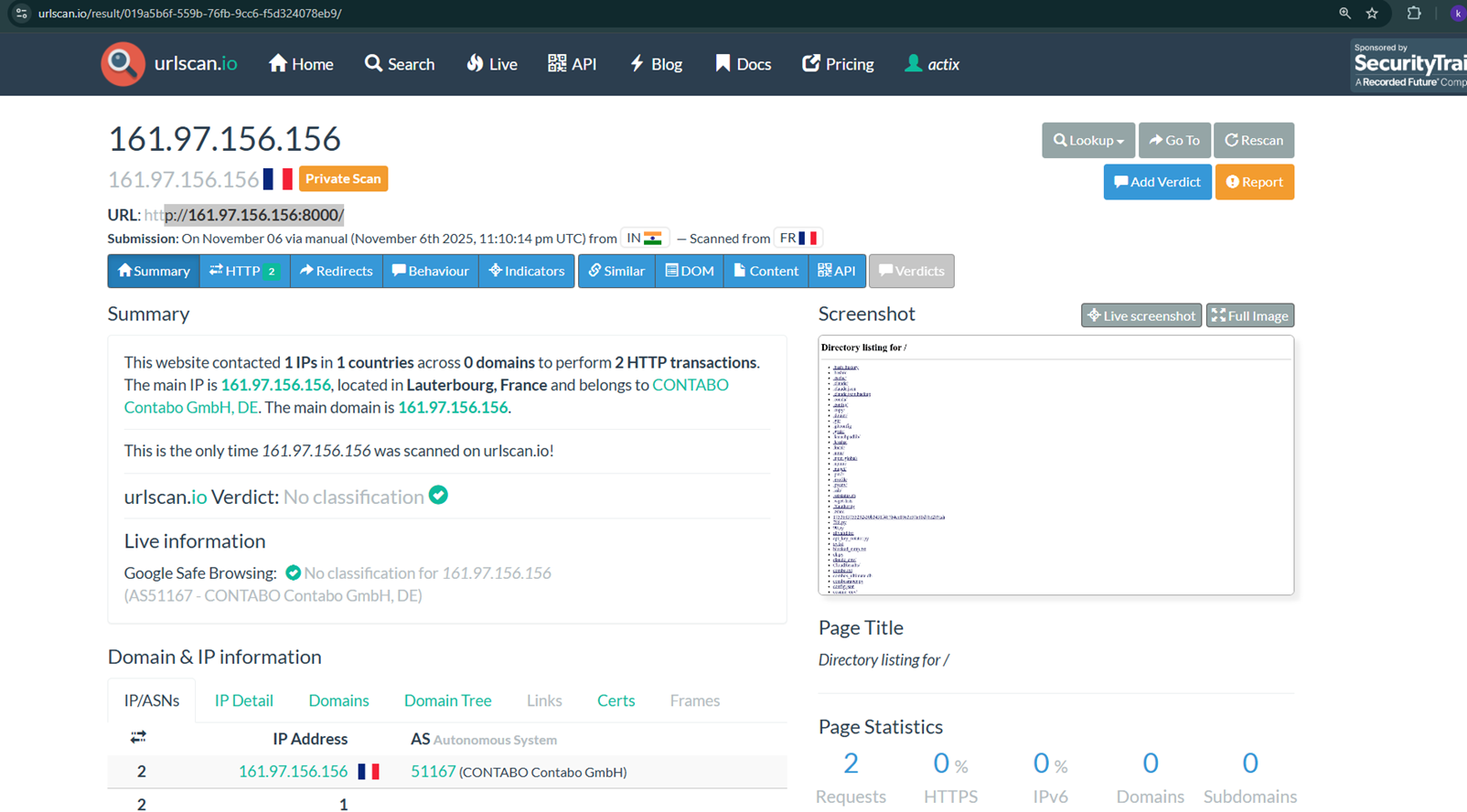
5 Command and Control Server Infrastructure Analysis: Directory Structure found at 161.97.156.156:8000
6 Recommendations For Security Teams
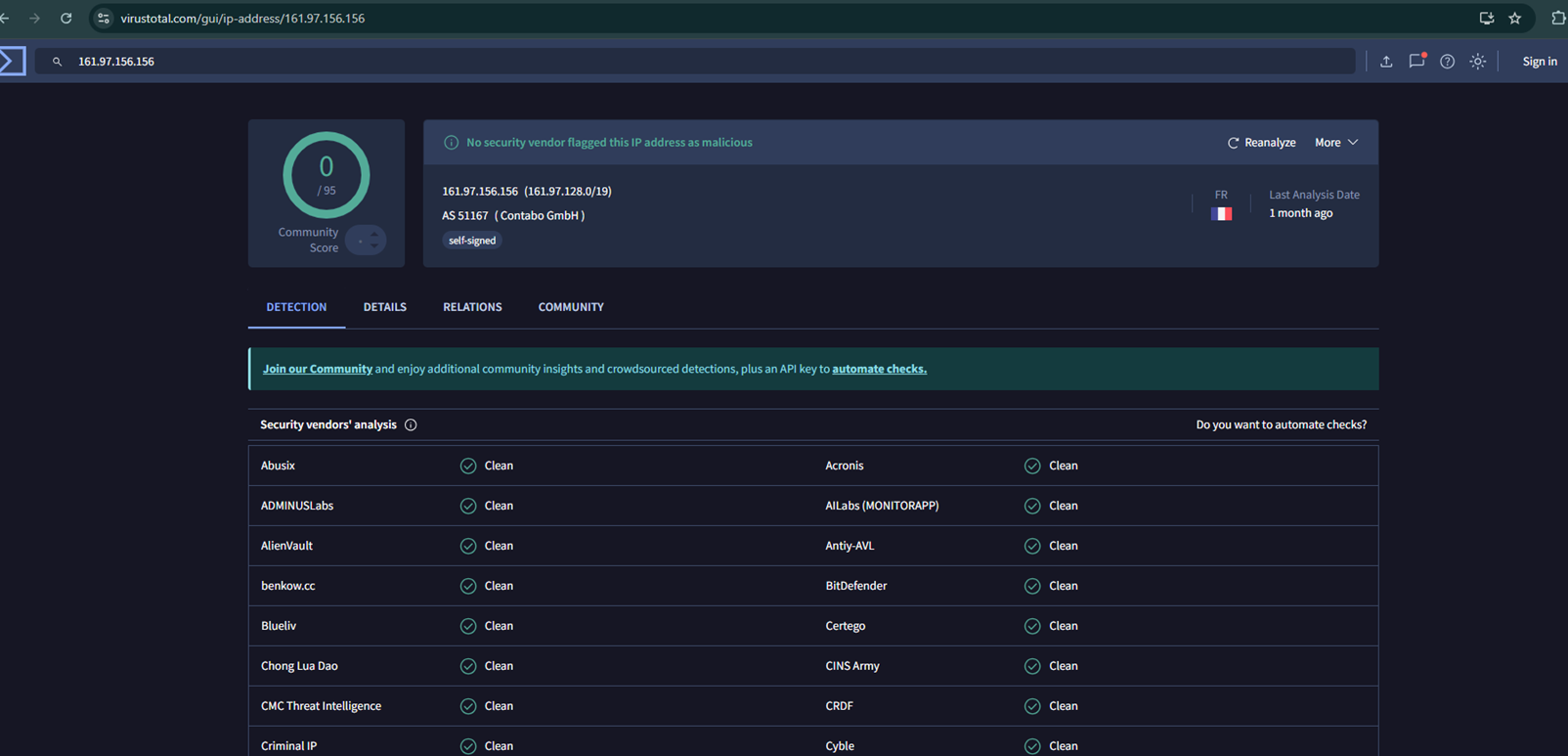
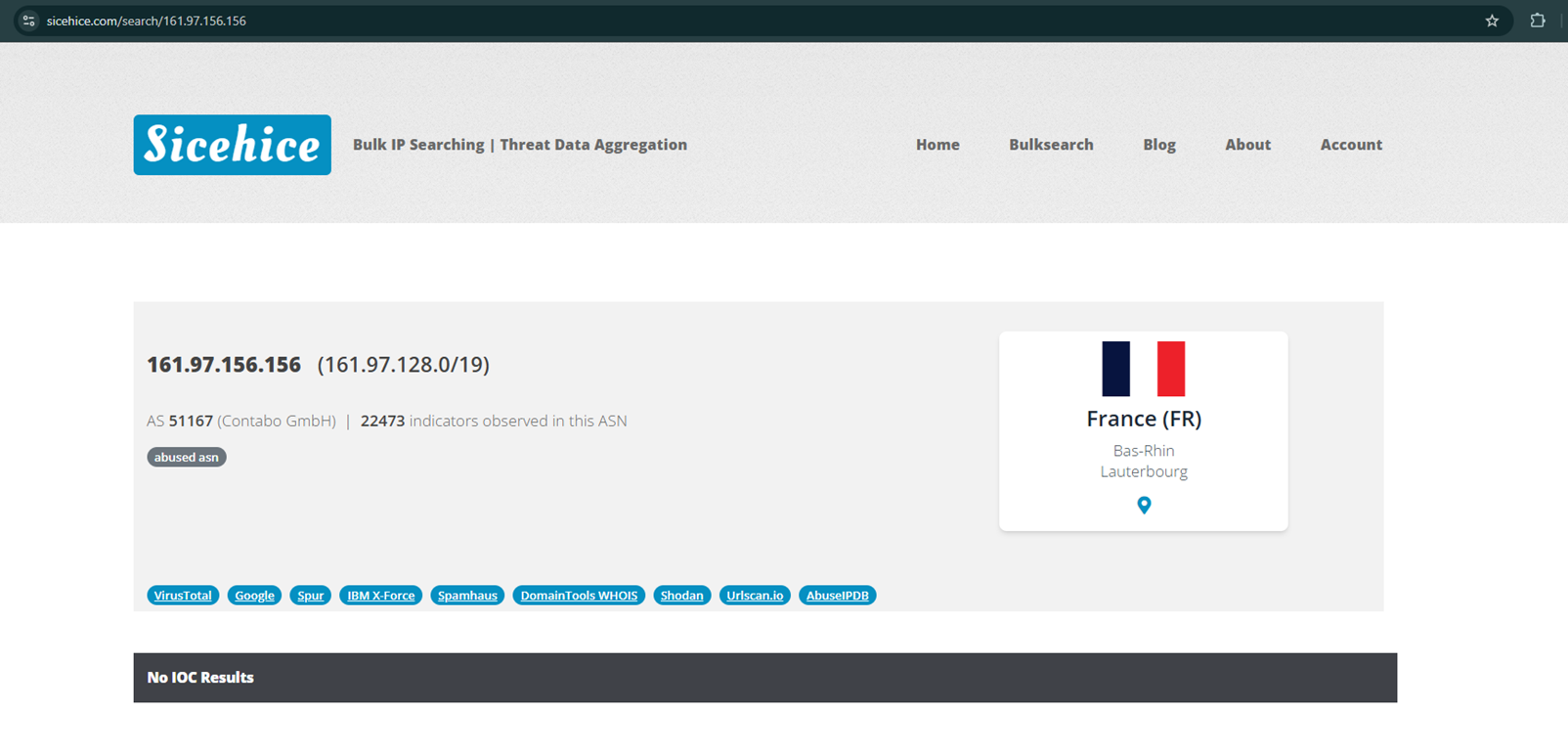
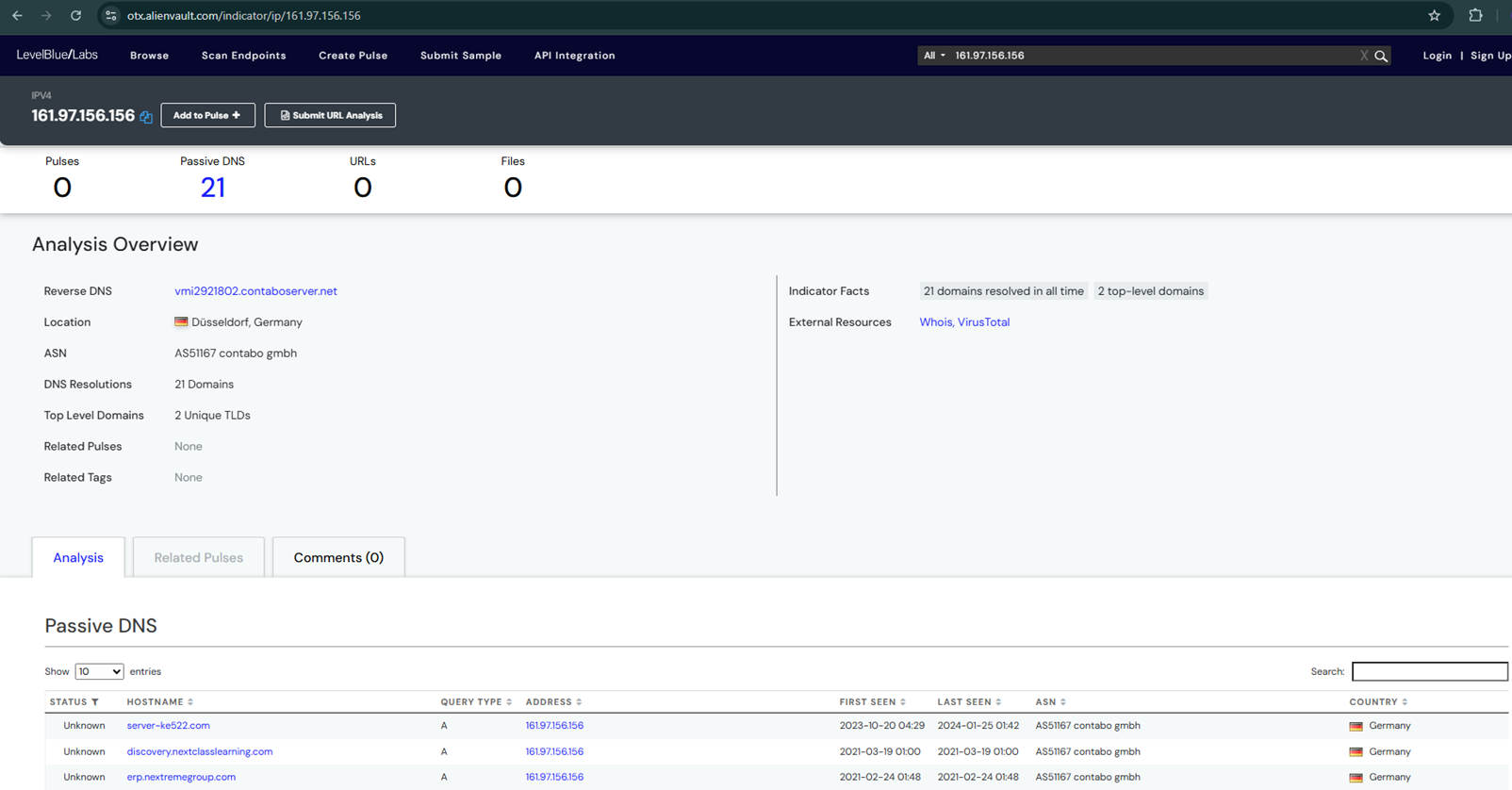
As per further analysis, this IP is not detected as malicious at various search engines like virustotal.com, sievehice.com, and alienvault.com, which suggests that malicious activity from this server is mostly blindsided now.
6.1 Fofa Search Engine
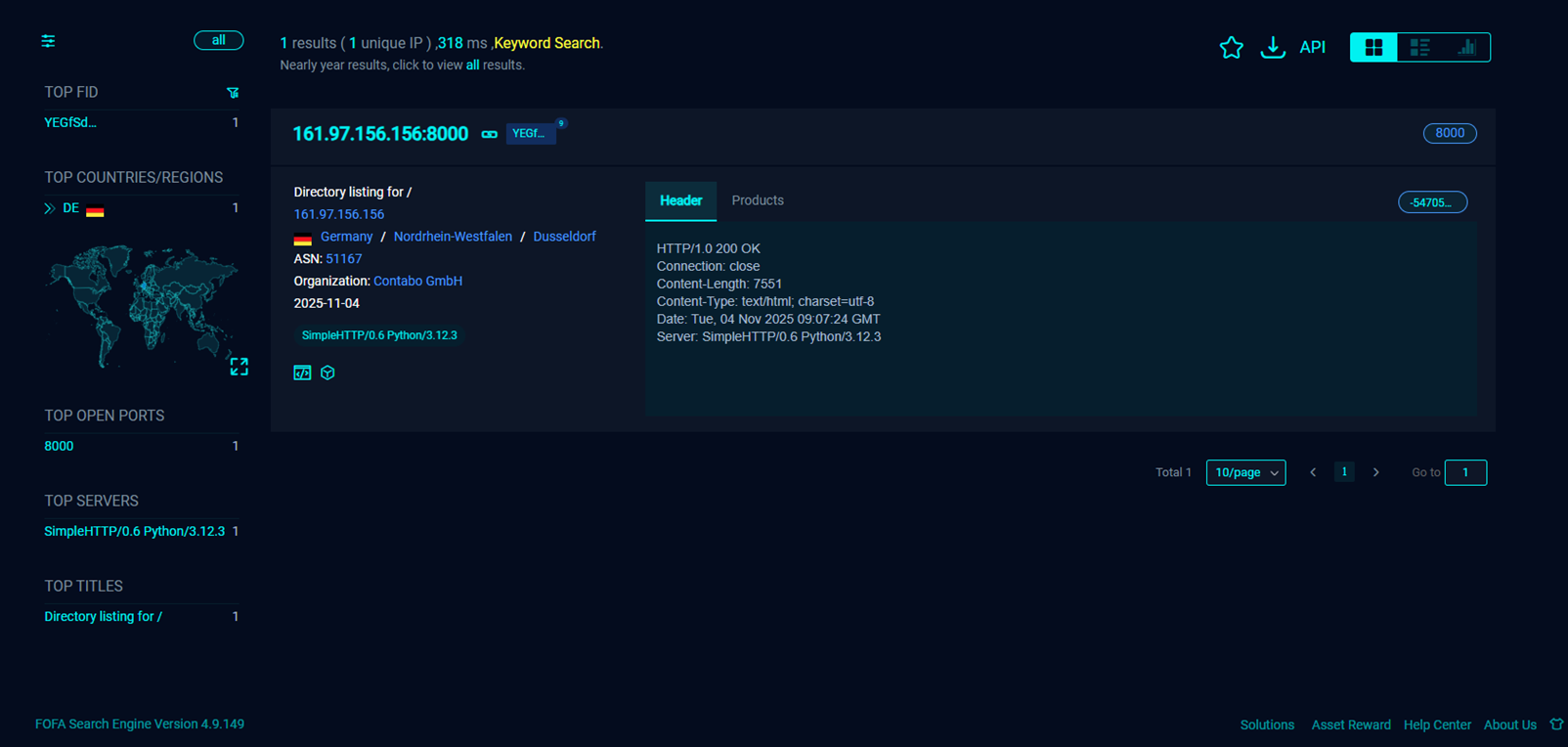
6.2 Censys
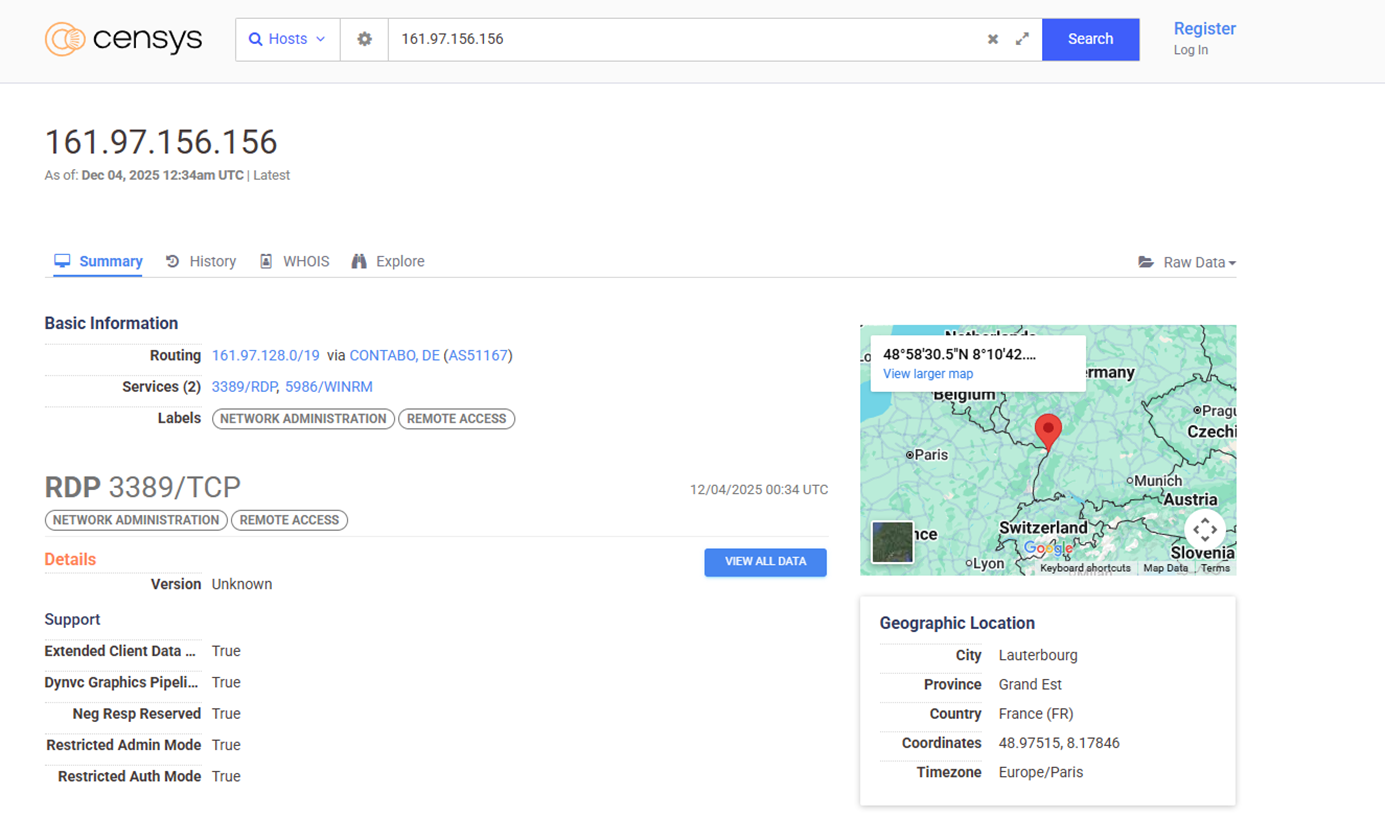
6.3 Virustotal
https://www.virustotal.com/gui/ip-address/161.97.156.156
6.4 Sicehice.com
https://sicehice.com/search/161.97.156.156
6.5 Alienvault.com
https://otx.alienvault.com/indicator/ip/161.97.156.156
7 Conclusion
7.1 Summary of findings
This report demonstrates that effective tool selection is inseparable from understanding the intent behind cybercriminal activity. By analyzing the infrastructure, behaviors, and technical artifacts observed, we identified clear indicators of the adversary’s objectives and operational maturity. Each phase of the investigation reinforced the need for structured, intelligence-driven methodologies in assessing cyber threats.
7.2 Reinforcement that tool selection reflects intent
The tools chosen for analysis were not arbitrary; they were selected specifically because they aligned with the threat actor’s observed tactics and the investigation’s intelligence requirements. Proper tool selection allowed us to accurately map the adversary’s capabilities, uncover hidden infrastructure, and validate hypotheses about operational intent. This reinforces a broader principle: the precision and relevance of analytical tools directly influence the reliability of the conclusions drawn.
7.3 Importance of monitoring cybercriminal infrastructure
Ongoing visibility into cybercriminal infrastructure remains essential. Threat actors continuously evolve their tactics, rotate domains, abuse legitimate services, and iterate malware payloads. Without sustained monitoring, defenders risk falling behind these shifts and losing opportunities to detect, attribute, and disrupt malicious operations. Continuous surveillance of threat infrastructure provides early warning signals that reduce response times and limit organizational impact.
7.4 Call to action for cybersecurity readiness
In an environment where adversaries adapt rapidly, organizations must strengthen their cybersecurity readiness. This includes maintaining threat-informed defenses, investing in proactive monitoring, updating detection capabilities, and fostering a culture of cyber awareness. By taking decisive action now, defenders can close visibility gaps, shorten incident response cycles, and build a resilient security posture capable of withstanding emerging threats
Want a deeper analysis? Reach out to us for a full technical report.
Request the full report → Contact us